Privileged Access Management with CyberArk

It shouldn’t be a surprise that protecting against cyber criminals requires a comprehensive strategy with collaboration among cybersecurity partners. It takes more than a single solution or product to tackle the constantly evolving threats. Collaboration and sharing knowledge are key to strengthen cybersecurity and effectively mitigate risk.
That’s we were excited to introduce Veritas 360 Defense. This architecture builds on our cyber-resiliency strengths and our partner ecosystem to empower organizations like yours to respond confidently to ransomware threats. With a focus on securing your data estate, Veritas 360 Defense unites data security, data protection, and data governance to support cyber-resiliency. You get the benefit of both proactive defense and reactive agility for every type of incident.
We also released Veritas NetBackup 10.3, which brings a revolutionary change to data protection with the introduction of the Credential Management System (CMS). This powerful tool enables the integration of external credential systems into the NetBackup ecosystem. CMS provides a simplified method to integrate credentials from trusted systems like CyberArk to:
- Augment security posture
- Ensure robust access control
- Mitigate risks associated with compromised credentials
In short, it makes credential management both more powerful and easier.
Why CyberArk and Veritas NetBackup?
In a continuous effort to fortify cybersecurity, we collaborated with CyberArk to integrate Veritas NetBackup with the CyberArk Privileged Access Management platform. This new integration reduces the risk of credential theft while allowing application owners a way to grant privileged access to data protection systems. The result, tight control of privileged access, access that can change retention setting that could put an organization at greater risk from ransomware attacks.
Features of the integration include the following:
- Automated Password Rotation: Regularly updating passwords to minimizing the risk posed by aged credentials is a fundamental pillar of robust cybersecurity. Use CyberArk comprehensive privileged access management solutions to automate password rotation and adherence to strong password policies.
- Elimination of Shared Account Passwords: CyberArk eliminates the risks associated with sharing passwords for elevated and privileged accounts. It provides a secure platform to manage and safeguard these critical access points, bolstering security and streamlining operations.
- Session Auditing for Malicious Activity Tracking: CyberArk's powerful session-auditing capabilities track user sessions for suspicious or malicious activities. This forensic trail is invaluable in investigations, allowing you to swiftly identify and respond to potential threats, minimizing damage and loss.
- Secure, Tamper-Proof Vault for Password Storage: CyberArk provides a fortified vault for password storage. This tamper-proof environment adds an extra layer of protection, safeguarding sensitive credentials from potential compromise.
Three Steps to Implement Veritas NetBackup and CyberArk
Step 1. Configure the vault. Set up the necessary accounts, policies, and access controls within the CyberArk Vault to manage credentials related to Veritas NetBackup interfaces or workloads.
Step 2. Install and configure Veritas plugins. Beginning with Release 10.3, NetBackup provides a CMS that allows you use external credential systems such as CyberArk. For NetBackup Appliances, install and configure the Veritas-specific plugins or connectors from the CyberArk marketplace. CyberArk and Veritas have developed plugins to guard all NetBackup interface access, including Webui, SSH, and IPMI.
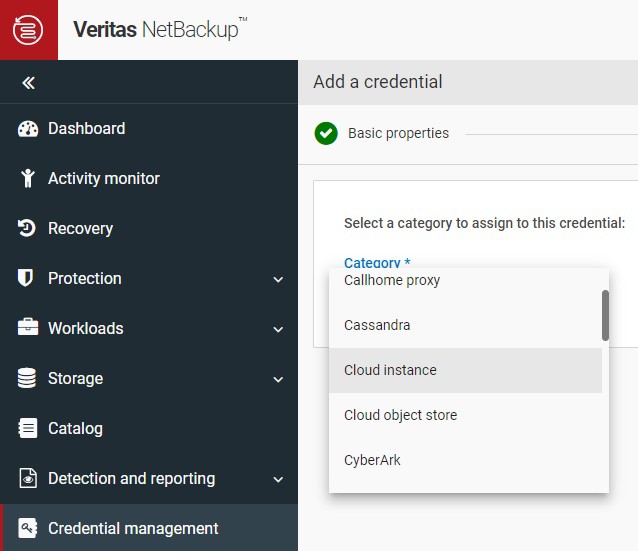
Step 3. Establish trust between the systems. Establish a secure communication channel between Veritas appliances and the CyberArk Vault. This may involve implementing network access controls to reduce attack surface. Veritas provides network access control allowing access only based on IP addresses.
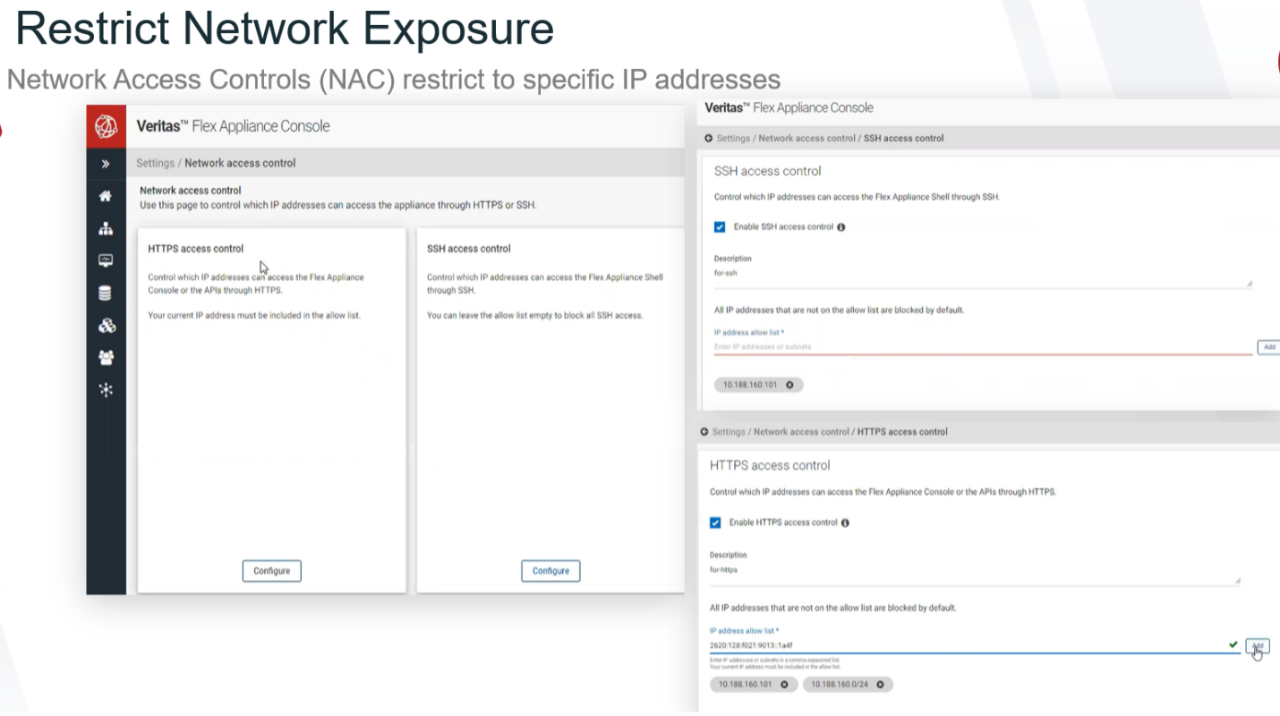
Use Veritas NetBackup and the CyberArk Privileged Access Platform to protect your data, your identity, and your privileged access. With CyberArk and Veritas on the job, you can focus on business. Together, we ensure that your data is available when you need it.
Learn more about the Veritas and CyberArk integration through the CyberArk Solution Brief.
