Protecting Healthcare’s Mission-Critical Applications and Data

Meeting HIPAA IT Compliance Requirements
The healthcare landscape is changing dramatically as digital strategies like virtual care, telemedicine, and unparalleled speed in online care collaboration open new avenues for faster, patient-centric care. This digital transformation underscores the need for data protection and compliance solutions to secure your healthcare organization’s mission-critical applications and patient data.
HIPAA Compliance
HIPAA requires that all hospitals and health systems, including medical practice, must be able to recover from a natural disaster. Failure to adequately recover from a disaster could lead to noncompliance and repercussions, such as fines or jail time.
Healthcare is one of the most important members of the first responders’ network. Every person, in the United States is affected by what happens in healthcare. The data Healthcare protects is a critical asset to the organization, and the protection of patient data is heavily regulated. Since 2021 there have been over 900 data breaches reported by the U.S. Department of Health and Human Services1. This year (2023) there have been over 350 breaches reported, as of August 1st. Many of these breaches are reported as “Hacking/IT Incident.” In each case, there are several users (patients) affected (from a few hundred to several Million). Obviously, not all breaches are created equal.
The question becomes how does Healthcare protect themselves from damages related to a breach (fines, bad publicity, and class action legal suits) that inevitably occur with each instance? One method is to truly understand their data. What does that mean? A sense of knowing what data is in the organization, where it is located and what each piece of data contains. Once an organization understands this, then they can act on what they have learned.
Successfully Meet Patient Care and Compliance Standards
They will need tools that scan the data and start understanding the metadata. Look for ownership, creation dates, file size, etc. Also, look at the security about and around the data. Are there Open Shares (folders that Everyone has read/write access), those who have access to folders (looking for outliers), or other individually defined security policies. A useful tool will also provide a means to remediate this issue.
We start by looking at the content of the data or classifying it. Looking for patient information is not an easy task. There are so many elements that become part of “personal metadata.” The basics would be name, addresses and phone numbers. From there we need to account for email addresses, birthdates, and other personal identifiers. Then there are the big important pieces: banking information, credit cards, doctor’s notes, prescriptions, and more. The classification process must be able to look for all these datapoints simultaneously. Do not forget images, prescriptions are regularly transmitted as images, so we need to account for those pieces of data as well.
Healthcare is looking for tools that can perform these tasks without affecting day-to-day work activity. These are not easy tasks to accomplish though. These tools do exist and are being used in a few Healthcare facilities. At this point, organizations can definitively say that they understand their data. So, what… They need a Third Phase, the actionability phase to make this process truly valuable. When we locate information that contains patient information, they need to act on what they have learned to protect it from “Hacking/IT Incidents.” When we think about classification, we need to look at the results. In all classifiers, a piece of data that meets the criteria of a classification policy is assigned a tag (or some identifier). This identifier can then become a point of action. A common action could be “to protect” that data, move it to encrypted storage. Data on encrypted storage cannot (today) be affected by malware. Therefore, this protects the healthcare organization from ransomware and data exfiltration.
Some of these tools can be used as an additional line of notification for a ransomware attack. Some tools can “see” large numbers of files being encrypted and notify administrators. They could also look for anomalous behavior, an individual copying data to a USB drive or other personal device. This could send another notification. The more these tools can do, the more they weave themselves into the overall security posture of the organization.
Why Veritas for Healthcare Cyber Compliance?
Veritas Data Insight answers many of these issues including HIPAA, HI TECH, and Stark Law today and provides some of the largest names in the Healthcare industry with the tools they need to protect their data. This suite of tools helps IT and Compliance departments intimately understand their data and allows them to act on what they learn.
Veritas Data Insight helps enterprises proactively assess and mitigate unstructured and sensitive data security risks. Organizations can classify sensitive data in a hybrid cloud environment and arm their operations team with the key knowledge needed to identify security threats and prepare compliance audits more efficiently. Combining data visibility, context and analytics across your whole infrastructure allows IT to gain relevant knowledge to improve data governance and resolve security, compliance, insider, and cyber threats quickly and conclusively.
The Veritas Integrated Classification Engine comes pre-loaded with patterns to detect around 1,200 sensitive data patterns such as date of birth, social security numbers, credit card numbers and medical records. It includes 275+ pre-configured policies for GDPR, HIPAA, and other regulations for different industries, and personal data policies relevant to 60+ different countries.
Rather than spend months on classification, Data Insight can classify on a targeted basis to comply with requirements in as little as time as possible. Healthcare customers can leverage Data Insight to use metadata across multiple content sources (including M365 and Cloud). It tracks security descriptors and uses user metadata to deliver intelligence. User metadata can include attributes like job function, department, and geo-location. Data Insight’s user behavior forensics help to build a baseline of activity metrics which can then be used to identify anomalies and trigger responses against policy. This information also feeds into understanding the value of data. The value is determined by assessing how many unique users interacted with a file and the level of transactions. It is then easier to differentiate between WORN (written once, read never) data versus data that is mission critical.
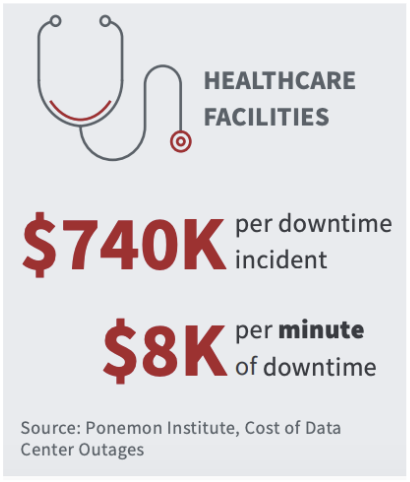
How can you get started to understand your Healthcare data Exposure?
Veritas offers a simple and rapid assessment to help identify where your organization can take steps to save millions of dollars on storage and locate risk that may be hiding where you least expect it. The Veritas Healthcare Data Assessment is an easy to deploy tool that scans your unstructured data, performs risk analysis, and delivers a comprehensive report in as little as 24 hours, giving you an immediate action plan to reduce risk and storage cost.
