Veritas Comments on NIST Cybersecurity Framework 2.0 Evolution
The National Institute of Standards and Technology (NIST) has played a pivotal role in shaping the cybersecurity landscape by developing the Cybersecurity Framework. NIST's initial release of the framework in 2014 served as a landmark document, offering guidance to organizations across various sectors in fortifying their cybersecurity postures. Recognizing the ever-evolving nature of cybersecurity threats and the need for continuous improvement, NIST has undertaken the ambitious task of drafting the Cybersecurity Framework 2.0.
NIST took an inclusive approach with a call for comments on the Cybersecurity Framework 2.0 draft, which signifies a critical juncture for the cybersecurity community. This revised framework aims to address the evolving threat landscape, technological advancements, and the expanding role of cybersecurity in our interconnected world. It reflects NIST's commitment to fostering a collaborative environment where stakeholders from government, industry, and academia can contribute to developing a that remains both relevant and effective.
Veritas Comments on NIST Cybersecurity Framework 2.0
When the call for feedback from diverse stakeholders was sent out, we felt Veritas Technologies, with over 80,000 customers relying on our holistic approach to data protection, recoverability, and compliance, we wanted to support the development of the CSF 2.0 Core and emphasize the importance of understanding data exposure before cybersecurity events.
In our comments on the CSF 2.0 draft, Veritas suggested that enterprises should classify and identify their data preemptively. We stressed the need to encompass all communication channels to address insider threats and compliance requirements effectively.
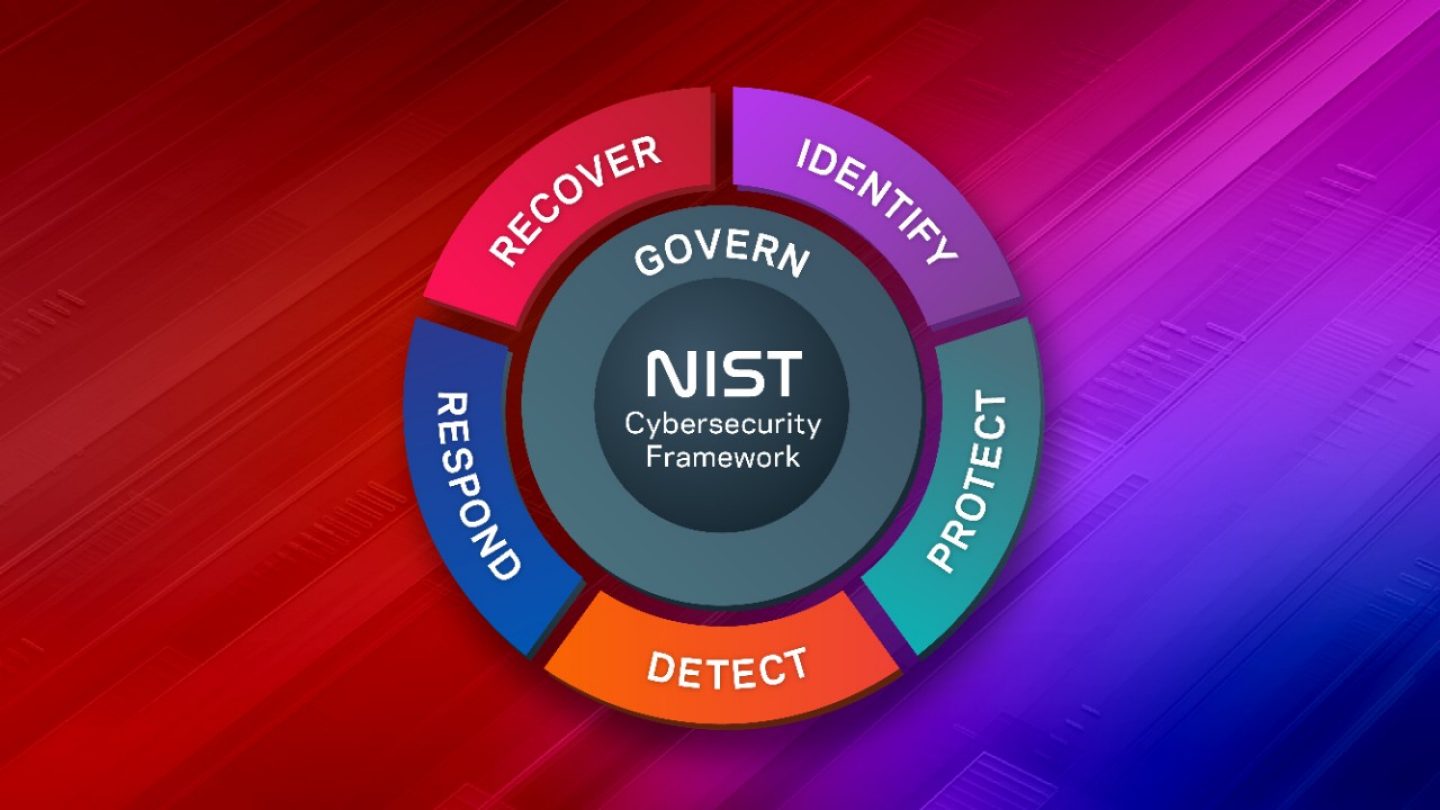
Recover
We recommended enhancing the language to "Restore and re-gain control," emphasizing the complexity of data recovery and the critical nature of understanding an organization's assets. We also recommended additional elements for Recovery Plan Execution, including:
- Review of, and recover in, an Isolated Recovery Environment
- Scan Immutable Backups
- Prioritize recovery of mission-critical data, applications, and assets
- Effective handling of evidence, such as logs and images, that will aid law enforcement to recover stolen assets
- Recovery must be included as part of ‘Standard Operating Procedures.’
Detect
Veritas advised securing backups through scans for confidence in recovery. Additionally, we proposed detailed elements to be added under "RECOVER (RC)," including reviewing isolated recovery environments, scanning immutable backups, and prioritizing recovery of critical data.
Govern
Veritas also proposed a more linear graphical representation of the Framework Functions, suggesting that "GOVERN" should span across all components, ensuring a comprehensive approach. Govern encompasses all the other aspects of CSF, but it is critical for enterprises to understand where their expose lies and need to know where their data lives in order to govern their data before the CSF event occurs.
NIST's release of CSF 2.0 marks a significant step towards improving cybersecurity. Veritas highlighted the collaborative effort needed to fortify cybersecurity landscapes, protect critical infrastructures, and adapt to evolving threats. Through engagement in this process, stakeholders contribute to shaping a more resilient cybersecurity framework for the future.
To learn more about the NIST Cybersecurity Framework 2.0, catch the replay of our most recent Veritas L!VE episode with Veritas Field Chief Information Security Officer, Joye Purser.
Demystifying the NIST 2.0 Framework
Watch the full Veritas L!VE episode on-demand.
The call for comments serves as a means for stakeholders to contribute their expertise, experiences, and recommendations to fine-tune the Cybersecurity Framework 2.0, ensuring that it remains a powerful tool for addressing the complex challenges of our digital age.
This collaborative effort holds the promise of fortifying the cybersecurity landscape and safeguarding critical infrastructures, economic assets, and personal information. By participating in this process, we worked together to shape the future of cybersecurity, making it more resilient and adaptive to the evolving threats of our interconnected world.
To learn more about NIST 2.0, check out the news release from earlier this week. For more information on how you can Protect, Detect, Recover, and Govern learn more about Veritas Cyber Resiliency and Ransomware solutions.
