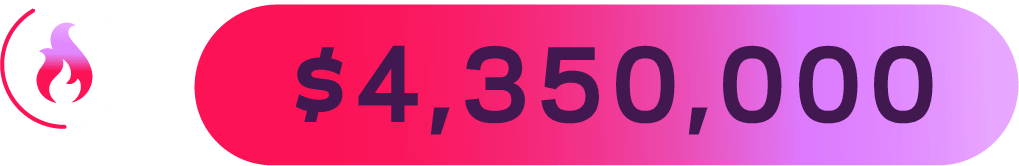
A ransomware attack happens 15 times every second.
Click.
Click.
|
When a cyber attack happens, there's a lot that can go wrong (or right!) depending on your data protection solution. Follow the sequence of events below to experience a cybersecurity breach from two very different perspectives:
With Veritas vs. Without



Intruder Alert!
A phishing attack, disguised as a cat video, unleashes malware on your organization. Anomaly detection identifies abnormal data transfers and triggers malware scans. Users restore files, servers, and services, while you and your team investigate and lock down your network.
Brief: Anomaly Detection
Video: Anomaly Detection, a Best Practice to Combat Ransomware
Ignorance is not cyber-bliss.
Without access to a Veritas malware scanning tool for backup data, this attack will go undetected, leaving the hackers to recon your environment. Similarly, without near real-time alerting of suspicious events, unstructured data can be exfiltrated without your knowledge.
Call of the hero.
You work quickly to stop ransomware from gaining control of your backups. Practicing Zero Trust Zero TrustDefinition:The Zero Trust security model describes a “never trust, always verify” approach to the design and implementation of IT systems. A Zero Trust strategy is based on continuous evaluation and verification of network access every time and for every single access. Not just users, but devices and workloads too. , you utilize immutable backups Immutable backupsDefinition:An immutable backup is a backup file that can’t be altered or deleted. Having an immutable backup ensures that you have a secure copy of recoverable data to protect against attacks or other data loss. and encrypted data. Near real-time alerts about accessed sensitive data allow you to swiftly identify and disable the compromised account.
White Paper: NetBackup Flex Scale
Brief: IT Analytics
White Paper: Recovery Vault
What you don't know can hurt you.
There’s a spike in Help Desk tickets. Something’s wrong, but without penetration test verification your vulnerabilities are unknown. Hackers are altering, erasing, and encrypting your data. Without secure-by-default immutability and indelibility, even your backups are at risk.
You vs Ransomware.
While grabbing a quick drink you receive an alert: malware has been detected. You begin flagging suspicious events for investigation. Instant rollback Instant rollbackDefinition:Instant Rollback for VMware facilitates a speedy recovery from a ransomware attack by restoring all affected systems and secure mission-critical apps and data directly to the production environment, standing up anything from an individual server to an entire data center in a matter of minutes. and instant access Instant accessDefinition:Instant Access allows VM and workload administrators to quickly access their virtual machine, browse for what they need, and get their data back, eliminating the reliance on backup administrators. shrink recovery times. Consistent policy-based solutions help to minimize data loss.
Technical Brief: Malware Scanning
White Paper: Isolated Recovery Environment
It's no contest.
The hackers are winning. IT admins struggle to access systems—including backup or recovery infrastructure. Productivity is plummeting, the company is losing money, and the pressure is high. Meanwhile, you are not even aware that cloud object storage is being deleted.
Business never ceases.
Maintaining business continuity is critical right now so you and your team work fast to restore key systems, such as SaaS workloads and business apps. Pivoting to forensic reporting, you locate the blast radius in your cloud data and alert the IT team where to focus their efforts.
White Paper: Veritas Alta™ SaaS Protection
Looking for a life jacket.
You’re swept up in a data breach tsunami—accounts locked, data compromised, and backups corrupted. And by not adhering to a shared responsibility model, you’re only now realizing that application reliability and data resiliency are YOUR problem.
Controlling the spread
Reviewing data access patterns, you identify patient zero and the point of infection. These findings lead to the compromised user accounts and exfiltrated data. Plans are already in place to mitigate the exfiltrated data, so you set them in motion.
Data Sheet: Data Protection for Cloud Workloads
Brief: Trust Nothing, Verify Everything
Chaos reigns
Operations have ceased, a ransom demand has been issued, and everyone is consumed by stress. Frantic, you try to identify which data and applications have been affected, but you don’t have the right tools. It won’t be long before regulatory and compliance issues are triggered.
Good night ransomware!
Ransomware thwarted and data restored, you are fully operational. Thanks to your robust cyber security response plan, you were able to quickly identify the risk and recover quickly using an unaffected backup image. You deserve that hot bath and a good night’s sleep.
Pressure to pay.
A sensitive document is posted online, which has customers worried and management on their heels. The pressure to pay the ransom is high. Meanwhile, with numerous cloud-hosted apps down, you are being confronted by frustrated employees who want answers and support.
A new day.
Battle-tested and energized, you and the IT teams are conducting a post-incident review. Areas of improvement are identified and discussed; test scenarios are updated. You’re feeling confident—when the next attack comes, and it will, you’ll be ready.
White Paper: Best Practices to Combat Ransomware
You've had enough, but have they?
The VP of Operations requests that you and the CTO determine how this breach occurred and formulate a plan for remediation. Unfortunately, with little to no forensics, zero-day is unknown, forcing the organization to recover from one-month old backups.
Practice makes perfect.
Coming on the heels of the attack, your invitations to the next recovery rehearsal are readily accepted across the organization. Everyone better appreciates the importance of these exercises and is eager to put all the recent learnings into practice.
White Paper: Preparing to Protect the Future
You've lost the battle and the war.
Another sensitive file is posted online, operations are frozen, data infrastructure is corrupted, and malware is still on the loose. There’s no leverage and little hope of recovering the data. With the tough questions left unanswered, you’ve been asked to step aside. Hey, someone had to take the fall.