Defend Your Data Estate—Anomaly and Malware Scanning Enhancements

This week, we made the exciting announcement to introduce Veritas 360 Defense, a new architecture that builds on our cyber-resiliency strengths to empower organizations to respond confidently to ransomware threats. With both a proactive and reactive approach to securing your data estate, the Veritas 360 Defense architecture is a blueprint for uniting data security, data protection, and data governance, guiding organizations through a cyber-resiliency strategy.
In addition to the many benefits accessible through our partner ecosystem of security vendors, Veritas 360 Defense introduces new cyber-resiliency features to the Veritas portfolio.
Anomaly Detection
Veritas anomaly detection is one of many ways to detect disruptions of normal behavior that indicate the presence of intended or unintended attacks. We have worked to continually improve the speed and efficiency of processing data to detect abnormal events, changes, or shifts in NetBackup datasets.
As part of this week’s announcement, we added a new rules engine and machine learning extensions that monitor user actions. You can now control how your system provisions Rule-Engine backend via Anomaly Detection settings within the web UI (Figure 1). The rules engine allows you to manage your alert level by providing specific threshold values, throwing an alert if your system goes beyond the threshold. For example, you can raise an anomaly if too many logins fail within a 10-minute span.
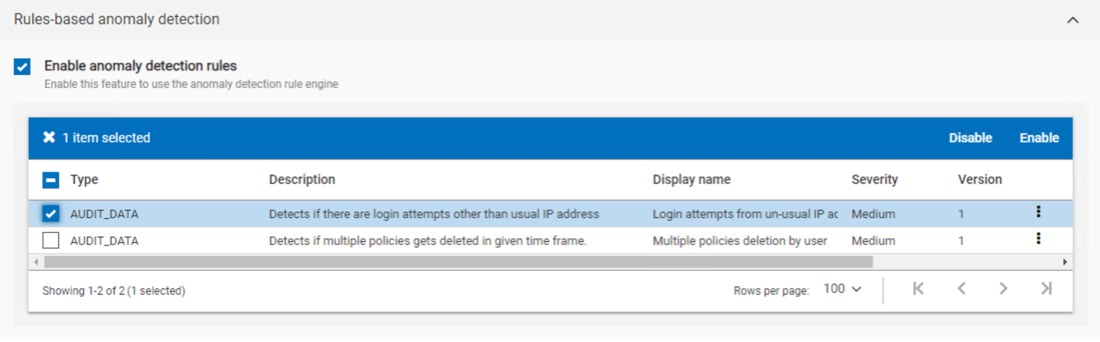
Figure 1: Enable and disable specific roles.
Our Veritas REDLab team has been monitoring and regularly executing real ransomware and malware attacks on our own products. This give us many advantages to study attacks, assess features that aid in detection, protect the backup repository and infrastructure, and speed recovery. The testing resulted in two new anomaly extensions to further enhance detection.
- The client-offline anomaly detection extension detects the failed backup of any malware-infected clients. These malware attacks generally encrypt data using ransomware deployed by attackers.
- The image-expiry anomaly detection extension detects any unusual manual image expirations or expiry-date modifications (causing early expirations). This capability will capture any destructive operations like expiring images. This new capability uses an ML-based model to form a normal trend of users who are expiring images manually or changing expiry dates. It accumulates the number of expirations/modifications done in given time window and forms a normal behavior per user. The extension will raise the anomaly if image expirations/modifications exceed the usual pattern. It will also will generate an anomaly if a new user that the ML model has not seen previously suddenly starts doing image expirations.
New Malware Scanning
We have expanded workload support for malware scanning to include Universal Shares, cloud VMs, and Kubernetes file-level data. Additional enhancements include a rescan of failed jobs from the point of failure so you don’t need to start over with a full rescan. It also generates a separate alert to report any skipped files as well as creates an infected file list.
Additional enhancements include scanning NetBackup backups for malware detection created on Open Storage Systems (OST) and AdvancedDisk storage types with supported backup policies (Figure 2). We have also established a framework for partners and expanded malware-scanning capabilities for OST targets to extend threat detection beyond the NetBackup ecosystem.
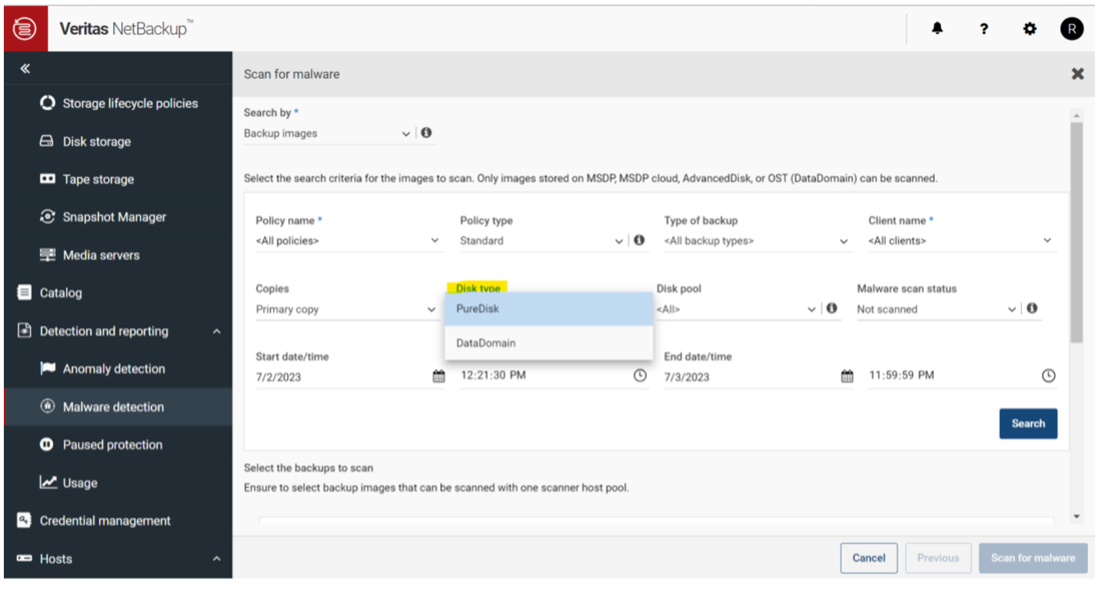
Figure 2: Support for filtering backup images for OST, AdvancedDisk, or PureDisk in the Disk Type filter.
Multi-person Authorization for Critical Operations
When enabled, the newly implemented multi-person authorization (MPA) prevents destructive data deletions by requiring approval from a user-designated individual prior to execution of the operation (Figure 3).
For instance, consider a scenario in which a user attempts to expire images through the WebUI or REST API. It generates a ticket instead of immediately executing the operation. The designated approvers have the authority to approve or reject the request. If the ticket is approved, the operation proceeds automatically. This advanced ticketing system also includes details on the requests and comments from approvers for audit and tracking purposes.
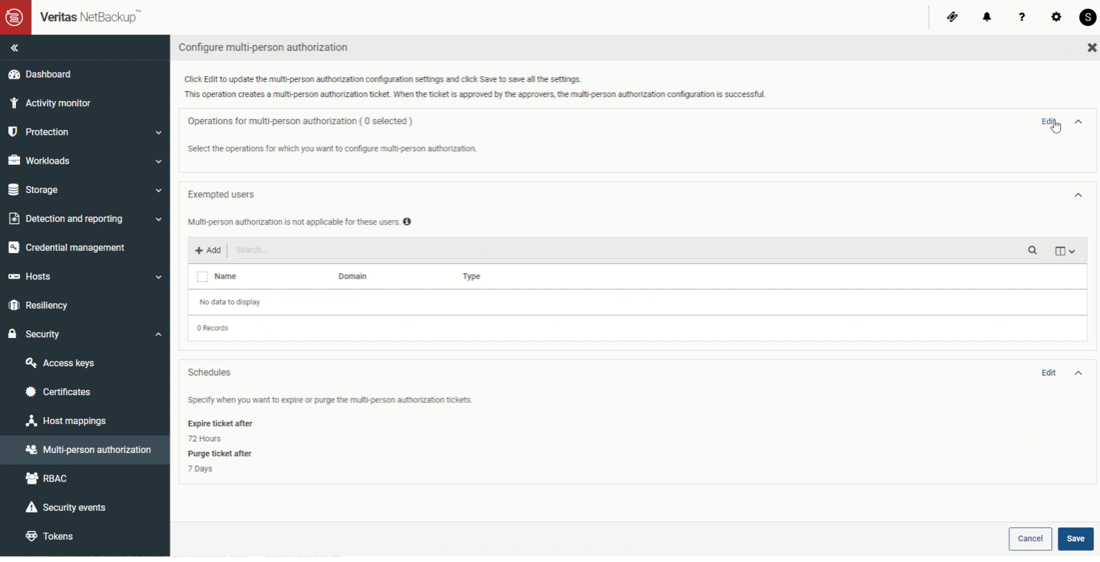
Figure 3: Multi-Person Authorization configuration.
Veritas 360 Defense
Anomaly detection and malware scanning are just some of the security enhancements in the latest release of Veritas Data Management Solutions. Learn more about our blueprint for defense in our solution overview.
