It should be Cybersecurity Awareness Month—every month!

This week closes out Cybersecurity Awareness Month, so there’s no better time than right now, this very second, to talk about all things cybersecurity and the importance of prioritizing ransomware resiliency. Especially this year, with how attacks have skyrocketed, it should be Cybersecurity Awareness Month—every month!
It’s hard to turn on the news without seeing another report on a major attack. Colonial Pipeline and JBS were high-profile attacks this year, with SolarWinds hackers continuing a barrage of attacks at this very moment! These come in addition to countless hospitals, computer manufacturers like Acer, and even the Washington DC Metropolitan Police Department. Noticeably, these attacks are targeted at infrastructure, government, and critical supply chain, with the end goal of gaining the biggest ransom payout. One that hit home recently was Ferrara, maker of my favorite Halloween treats like Nerds, Lemonheads, and SweeTarts! Hitting a major candy manufacturer right before Halloween, clearly a strategically timed play for maximum panic.

Veritas L!VE
We recently invited Karen Evans (former CIO for the U.S. Department of Homeland Security), Joseph Davis (Microsoft Chief Security Advisor for Healthcare in the U.S.), and our very own CISO, Payman Armin, to share their cybersecurity insights, advice, and perspective in our latest Veritas L!VE episode.
The show kicked off with host Anthony Cusimano asking the guests, “What has been the biggest “wow” moment in your career in relation to cybersecurity?” Hearing all their stories was great! Memorable share was from Karen Evans and her story around web caching. You will have to watch to find out more!
The highlight for me was the discussion around future expectations and what needs to be done to drive the importance of cyber acumen. Guest Joseph Davis shared key points regarding arming everyone in the organization with the education and tools to be secure, “The bad actors are very smart, agile and flexible. They are not under the same constraints. We have to follow the rules. We have to follow policy. The attackers have none of those constraints. As consumers, we must think about all the ways in which we can be taken advantage of and that will help make us all educated consumers.” I agree with Joseph, we all have a part to play in cybersecurity and prevention of attacks.
Guest Karen Evans shared some insight into risk posture. “We are at an inflection point, now society as a whole, has seen many of the consequences of not paying attention to cybersecurity…What it all comes down to is risk posture. Do I forgo certain risks, because I want short-term gains or do I actually invest into the future so that I have long-term gains. That is a balancing act that all small, medium, large, and governments really have to wrestle with now.”
If you missed the episode, make sure to catch the recording here
It is not getting better, it is getting worse.
Some harsh reality here, it is a crisis. Everyone should feel a sense of urgency to prioritize cybersecurity hygiene and implement best practices immediately. So, let's talk about why? Bad actors are getting savvier and more sophisticated. Gone are the old days where hackers were amateur kids in their parents’ basements, looking for a challenge or bragging rights for their friends! Today, Ransomware-as-a-Service vendors exist in large numbers and have successfully transitioned to a highly profitable business model with the charter of successfully crippling organizations at their most vulnerable times to maximize ransoms. These businesses provide turnkey code, tools for encryption, communicate with victims, facilitate ransom note collection, and have an advanced support network with helplines. Compound that with the inflated value of cryptocurrencies like Bitcoin, now attacks are even more lucrative for bad actors. Add in the complication of the sudden WFH model and acceleration of new technologies, and the past year was a perfect storm for bad actors to take advantage of vulnerabilities!
What this now means for all of us?
Security tools and technologies are incredibly important, but alone, they are insufficient. It is time for a complete mindset shift to implementing a solid, multi-layered cybersecurity strategy that ensures no single point of failure, no unauthorized access, complete visibility, and strategically reduced attack surface with solid recovery options.
The Veritas Ransomware Resiliency Solution.
At Veritas, security and cybersecurity hygiene have been part of our DNA for years. Our solutions help combat the threat of ransomware by providing a comprehensive, multilayered approach that extends beyond data protection. Here is a quick summary!
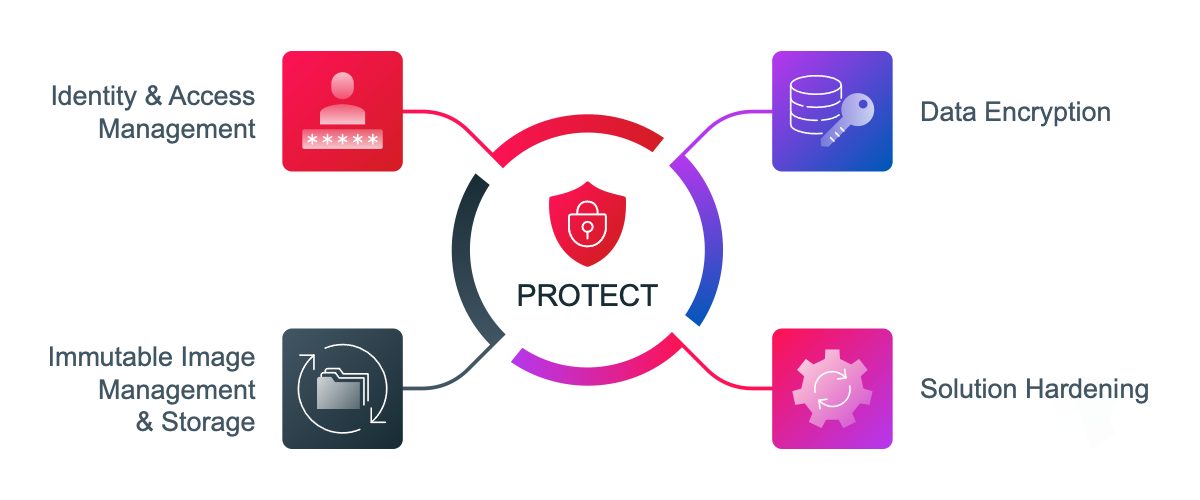
PROTECT
Veritas safeguards your data’s integrity and reduces risk, everywhere, with system hardening, immutable and indelible storage (with internally managed compliance clock), data encryption (both in-flight and at-rest to prevent data exfiltration), and identity and access management including MFA and RBAC.
DETECT
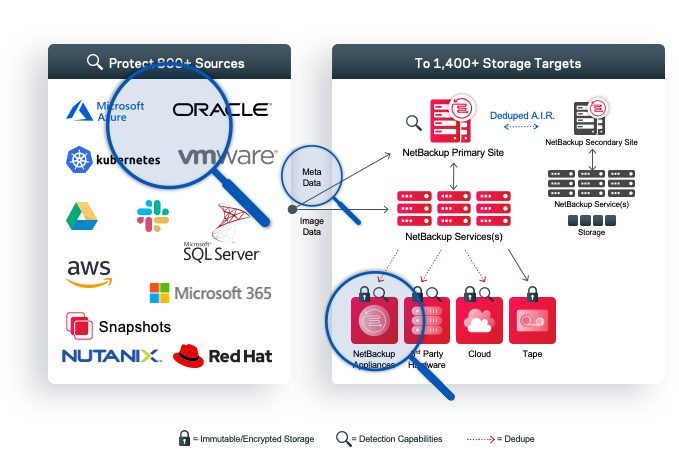
Veritas provides solutions that detect threats and enable monitoring of your entire environment. That is everything, including edge, core, and cloud. Only Veritas can cross-reference all of your servers and storage with all of your backup vendors, yes even competitive solutions, to ensure no servers fall through the cracks and are left vulnerable to ransomware.
RECOVER
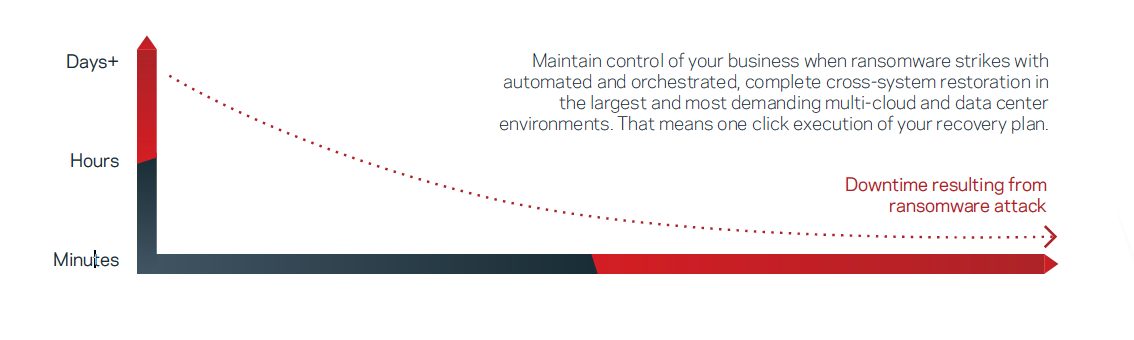
Maintain control of your business when ransomware strikes with automated and orchestrated, complete cross-system restoration in the largest and most demanding multi-cloud and data center environments, with the click of a button. One-click execution of your recovery plans.
Want to learn more?
Check out these recent ransomware resiliency blogs from some of my esteemed colleagues:
- Running Kubernetes? Do These Eight Things to Secure Your Data and Workloads
- The value of APIs for the Resilient Enterprise
- Recover one or 100 virtual machines with bulk instant recovery for VMware
- AI-Powered Anomaly Detection with NetBackup
- Overcome the inevitable storm of ransomware with NetBackup
- First known malware to operate exclusively from within a container
- Ten Ways Your Employees Can Help Prevent Ransomware Attacks
- Ransomware: A Blueprint for Practical Success and Transformational Outcomes in Three Easy Steps
- Ransomware Resiliency and a Modern Air Gap Solution
The threat is real.
Do Your Part. #BeCyberSmart."
