NetBackup Supports AWS PrivateLink for Amazon S3

AWS recently announced the general availability for AWS PrivateLink for Amazon S3. AWS PrivateLink provides private network connectivity between Amazon Simple Storage Service (S3) and on-premises resources which use private IP addressing from your virtual network. This eliminates the need to deploy proxy servers which typically constrain performance, add single points of failure, and increase operational complexity. With AWS PrivateLink you can now access S3 directly as a private endpoint using your secure, virtual network which leverages a new interface endpoint within your Virtual Private Cloud (VPC). This new feature extends functionality for existing gateway endpoints by enabling users to access S3 using private IP addresses. NetBackup API and secure HTTP requests to S3 can now be automatically directed through interface endpoints that connect to S3 securely and privately via PrivateLink.
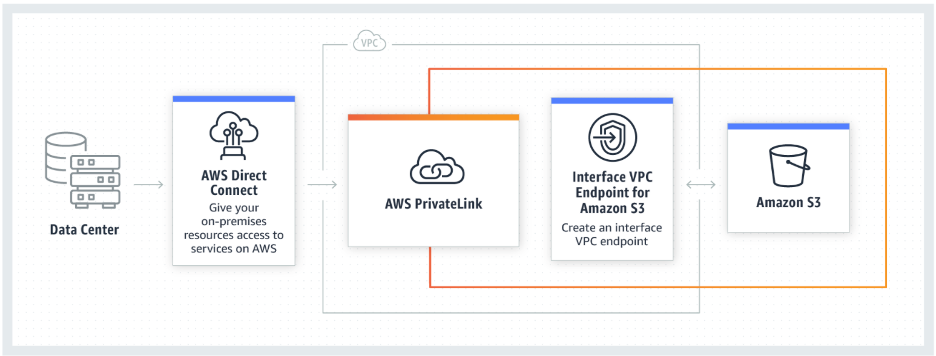
Interface endpoints simplify the NetBackup network architecture when connecting to S3 by eliminating the need to deploy an internet gateway or configure firewall rules. Additional visibility with your network traffic can now be realized with the ability to capture and monitor flow logs within your VPC. Finally, you can take additional security measures with your interface endpoints by creating security groups and enabling access control policies.
Securing NetBackup Data Between the Data Center and AWS S3
The AWS Shared Responsibility Model defines the distribution of security responsibilities between AWS and its customers. One of the biggest concerns that influence cloud adoption is security. In the context of data protection to the cloud the transport remains an area of concern for many organizations that are subject to data regulatory and/or compliance requirements. NetBackup users can now safely transfer data to and from the AWS cloud without the risk of exposing sensitive data to visibility, tampering or theft. Veritas has thoroughly tested NetBackup with AWS PrivateLink to send backup data as well as recover to and from AWS S3. We are also proud to announce that NetBackup provides day-zero support for AWS PrivateLink.
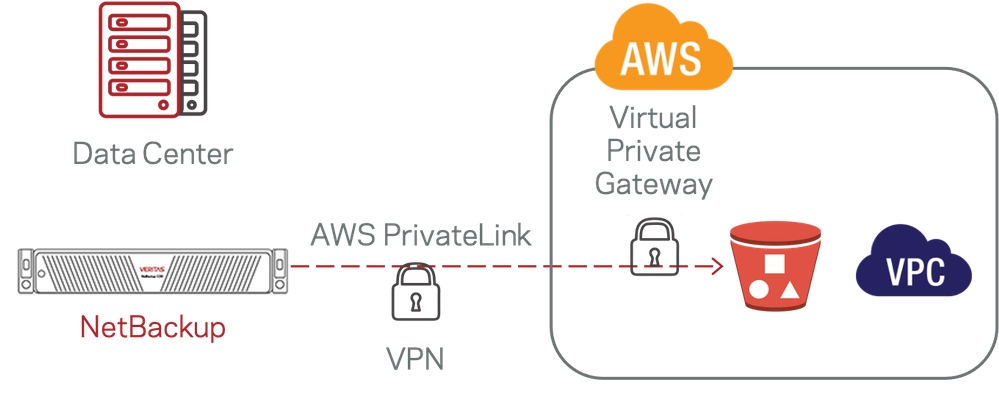
The high-level diagram illustrated below shows the test environment Veritas setup to validate NetBackup support for AWS PrivateLink S3. Veritas selected an AWS VPN approach for solution validation testing and the steps outlined below were completed through the AWS console:
- Create a Virtual Private Cloud (VPC) if one doesn't exist.
- Configure the VPC IP range, specific to the private network being deployed.
- Add an S3 Interface endpoint to the VPC. This is the actual PrivateLink.
- Create a Virtual Private Gateway (VPG) and attach it to the VPC.
- Create a Site-to-Site VPN, used to connect from on-premise to AWS.
- Add the subnet for the on-premise server to the VPN and VPC subnet routing tables.
- Create an AWS Customer Gateway (CGW).
- Download the CGW configuration file for the router model being used and configure the VPN.
- Configure the Customer Gateway with the IP from the VPN configuration.
- Add the on-premise IP CIDR to the VPN routing table.
- Connect to the AWS S3 endpoint from the on-premise server.
The test plan focused on two primary objectives which were validating basic connectivity and functional testing.
- Basic connectivity testing - NetBackup RHEL primary|media |client running in EC2 instance:
- Configure NetBackup Cloud Storage Server to connect to AWS through a PrivateLink endpoint
- Verify basic backup, expire, import, verify, and restore capabilities
- Verify that traffic is running through AWS PrivateLink
- Functional testing – NetBackup primary |media |client running on RHEL & Windows servers:
- Configure NetBackup Cloud Storage Server to connect to AWS S3 |Glacier through classic cloud connector (with compression enabled) and PrivateLink endpoint
- Verify basic backup, expire, import, verify, and restore capabilities
- Verify that traffic is running through AWS PrivateLink
- Run automated Cloud certification test suites:
- Basic Open Storage Cloud Storage Server
- Basic backup, expire, import, verify, and restore
- Full-Backup with True Image Restore (with and without move detection)
- Cumulative, differential incremental backups | restores
- Backups | restores of large files, encrypted files, compressed files
- Checkpointed backup interrupted and resumed
- Optimized Synthetic backups | restores
- Accelerator-enabled backups | restores
- Server-side Encryption
- Configuration
- Basic backup, expire, import, verify, and restore
- Accelerator-enabled backups | restores
- Test importing images after expiration from NetBackup catalog
- Run backup and restore testing using each of the retrieval options
For additional details and more information please refer to the links below:
https://www.veritas.com/protection/netbackup
https://aws.amazon.com/blogs/aws/aws-privatelink-for-amazon-s3-now-available/
