Ransomware: A Blueprint for Practical Success and Transformational Outcomes in Three Easy Steps

Although a cybersecurity or ransomware attack can be potentially crippling, the very rational fear of such a threat will revolutionize how we manage our most critical currency, information. The perceived costs of a breach, both direct and indirect, will force smart organizations to quickly adapt to these new market conditions. Global actors on this stage will ultimately make smart investments in the short-term to realize a wholesale change in the management of information. In the end, these investments will have the benefit of drastically reducing risk, cost, and complexity while bettering our collective end user experience. Given the exponential growth of the world’s data, this cyber headwind will positively transform the digital world and as a result, impact every industry.
The potential impact of ransomware attacks is very real and financially paralyzing. As noted in the Harvard Business Review, ransomware attacks increased by 150% in 2020 and the amount paid out by victims of these attacks grew by 300% (Sharton). The latest forecast indicates that known damages associated with ransomware attacks will exceed $20 billion in 2021 which represents a 57x increase over 2015 (Morgan). Quite simply, not creating a ransomware-resilient organization could fall into the class of managerial negligence.
The exciting news is this cyber concern will transform how organizations consume and manage information, ultimately for the better. A new blueprint for more effective information management will emerge as the winner of this turbulent time. Traditional platforms that wholistically “touch” enterprise data as a course of normal business will drive immense change. To apply a practical perspective to the exchange, Veritas Technologies [Veritas] will be discussed given their market leading position in the availability, protection and insights of data, for on-premises, hybrid and cloud workloads. The desired outcome will be to define a consumable path, or blueprint, to ensure ransomware resiliency.
THE THREE-STEP APPROACH
When one thinks of ransomware, history would dictate that an attack will happen, and remediation will be required. The defining point will be how much damage does the attack cause, financially and otherwise. At the most rudimentary level, one should be concerned with the protection of all critical (valuable) information, the ability to detect potential ransomware threats, and ensure a quick automated recovery (restore) of an entire business application, if needed. This progression, a simple three-step framework, supports the protect, detect, and recover components of an organization’s overall cybersecurity strategy. We will unpack each of these elements and reference Veritas’ Enterprise Data Services to add real-world context.
STEP 1: PROTECT
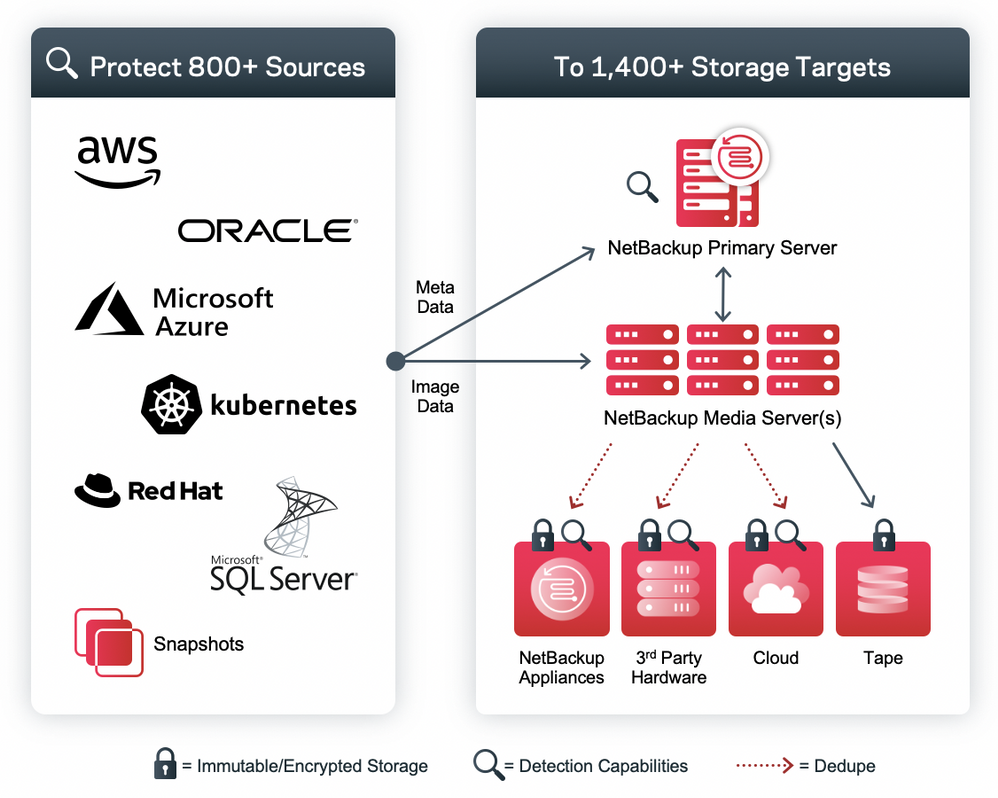
The first step in any sound ransomware mitigation plan is to ensure the protection of all relevant data. Several disciplines are required to safeguard data integrity, but a critical aspect is backup and recovery capabilities. It is vital that these backups include data encryption (both in-flight and at-rest to prevent data exfiltration), immutable and indelible storage (with internally managed compliance clock), server/software hardening (with zero trust access to ensure data integrity), and simple recoverability (data and servers are required). As important, those restores must be efficient and viable in third-party facilities like AWS, Microsoft Azure, and Google Cloud. Such data protection solutions must encompass the protection of all enterprise workloads, regardless of location. Veritas’ NetBackup platform addresses all the above requirements at enterprise scale.
STEP 2: DETECT
To take the next step towards ransomware resiliency, one must harness the power of ransomware anomaly detection. The efficacy of anomaly detection is, in part, a function of the amount (volume), scope, and type of data being analyzed. Companies, like Veritas, that touch a massive amount of data throughout its lifecycle (cradle to grave) across the entire enterprise, have a strategic advantage. The ability to correlate outliers associated with ransomware attacks affords organization quick levels of responsiveness and an accurate time of recovery (rollback point) if a threat is discovered. As it relates to Veritas, customers leveraging the latest version of Veritas NetBackup data protection will receive the benefits of ML based automated ransomware anomaly detection within the data protection environment. This is a great start, but more can be done.
Specifically, Veritas’ infrastructure optimization platform extension (APTARE™ IT Analytics), agentlessly correlates and analyzes north of 50,000 unique points of interest. Originally developed to optimize infrastructure and operations, APTARE’s capabilities have expanded to offer anomaly detection. Having this multi-vendor, panoptic view of IT (storage, compute, backup, etc.) across your entire environment, on-premises or cloud, is important in validating that all enterprise data is properly protected. Additionally, Veritas’ Data Insight platform extension allows one to truly unpack file level data (unstructured) to help define ownership, classify, locate PII, automate compliance, etc. Again, ransomware anomaly detection is also included in this analysis.
Collectively the Veritas solutions empower organizations to illuminate anomalies in their primary data as well as their data protection (backup) environment, across their entire infrastructure and within the files themselves. The ability to monitor and report on these vulnerabilities across such a broad range of data sources is invaluable in effectively managing such threat vectors. It is important to note that the above assumes standard vulnerability scans would be a normal course of business.
STEP 3: RECOVER
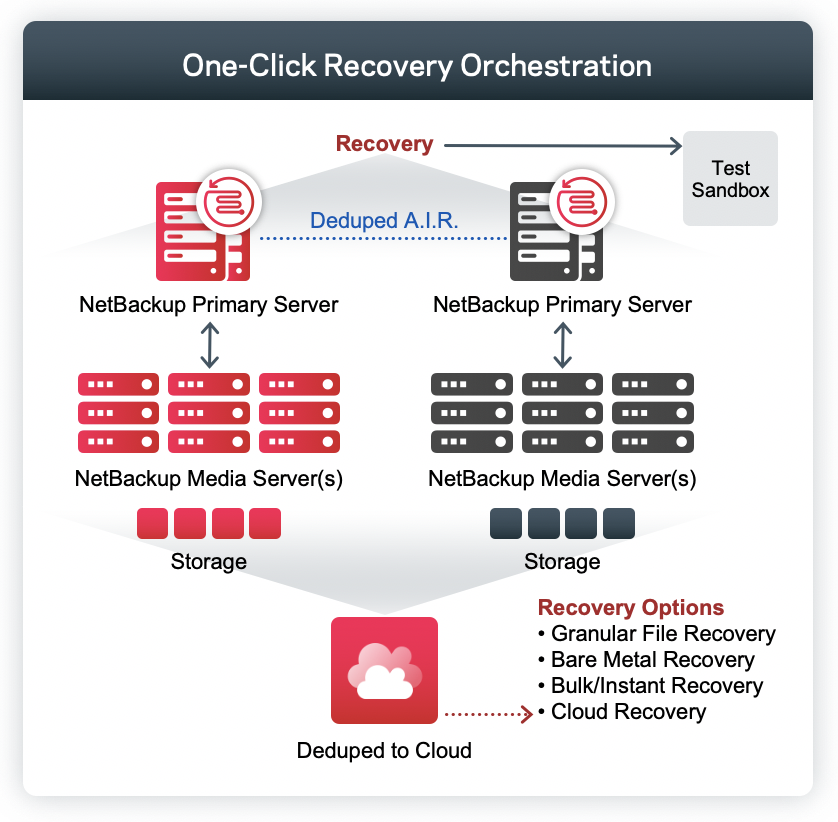
The third and final step of our ransomware resiliency path is recovery. In order to ensure recovery, one must add true multi-site, application aware, resiliency to the mix for the ultimate ransomware mitigation blueprint. Once a significant breach, or disaster hits, it is vital to have a trusted platform to simply automate and orchestrate a complete cross-site, or cloud, restoration with the click of a button. The ability to do so, especially at scale and with minimal infrastructure will dictate the level of organizational preparedness and overall resilience. In the case of Veritas, all this functionality is included in the core of the data protection platform. Not only will the data be accessible, but the applications will also be online with all the necessary dependencies.
WORLD-CLASS RANSOMWARE MITIGATION STRATEGY
As outlined above, a world-class ransomware mitigation strategy can be found in a refined protect, detect, and recover strategy. As alluded to in the introductory paragraph, companies who fully embrace the protect, detect, and recover strategy with Veritas, will realize a very significant reduction in cost, complexity, and risk. The core purpose of many of these solutions is to illuminate data while managing availability, protection, and compliance.
By properly mitigating ransomware risks, one must illuminate and analyze data across the enterprise. If fully executed, organizations can expect to manage far less with much more clarity. The Global Databerg Report finds that with most enterprise entities, 85% of data is redundant, outdated, or trivial [ROT] (Veritas). An ancillary benefit of proper Ransomware mitigation, with the Veritas platform, is that one can determine the true nature of a given file and make informed decisions as to how to best manage, or delete, it. Many files are only under IT management because said files are functionally ownerless and organizations do not know how to effectively manage them at scale. Imagine being able to determine if a file includes PII, define the defacto owner (usage, access, content, or properties), disclose the last time accessed, determine the corporate relevancy, validate user access compliance, automatically classify the file, etc. Thereafter, one can intelligently automate the management, movement or deletion of a given file while keeping accurate and defensible records. This is exactly the outcome one can expect from the Veritas platform. The result of this data illumination and automation is the ability to safeguard compliance while judiciously segmenting how a given bit of information is managed while following the above ransom attack blueprint. Given the amount of redundant, trivial, and outdated information in the hollows of most enterprises, managing far less data better ultimately extracts cost, betters the end user experience, and reduces risk of a cyber incident.
LONG-TERM IMPACT
The after-effects of ransomware attacks have had a dire effect on the economy, social trust and information management. The silver lining is that the long-term impact will be one that favorably changes how we manage information, one of our most precious assets and the new world currency. The above perspective offers a blueprint for effective and efficient ransomware mitigation and the noted Veritas solutions can be harnessed immediately yielding improved end user experience and considerable reduction in cost, risk, and complexity. The future is very bright for those who chose to leverage this opportunity to change how information is managed.
