The New Normal, Hackers Are Logging In

Harsh truth: Innovative technologies are enabling new tactics for cybercriminals. Using exploited credentials is easier and faster than hacking in through privilege escalation or other means. Today, we know that most cyber criminals log in; they don't bother to hack. In 2022, the volume of password attacks soared to an estimated 921 attacks every second, according to the Microsoft Digital Defense Report 2022. Criminals do this in a variety of ways. Let’s explore the top methods and tips for how to combat them.
Method #1: Password Hacking
Cyber criminals take advantage of security weariness and simply guess passwords. They most commonly utilize brute-force attacks, leveraging trial and error to guess the password with automated tools. These attacks, along with dark web password lists and defaults like "Password123," grant rapid access to otherwise sound systems when compared to cookie theft, UI redress, or keylogger injection strategies. Additionally, they leverage social engineering to guess passwords based on information gathered from social media posts like names of spouses, kids, or pets. Once they gain access with a login to an enterprise account, cyber criminals bypass security controls and engage in lateral attacks, potentially gaining access to critical data.
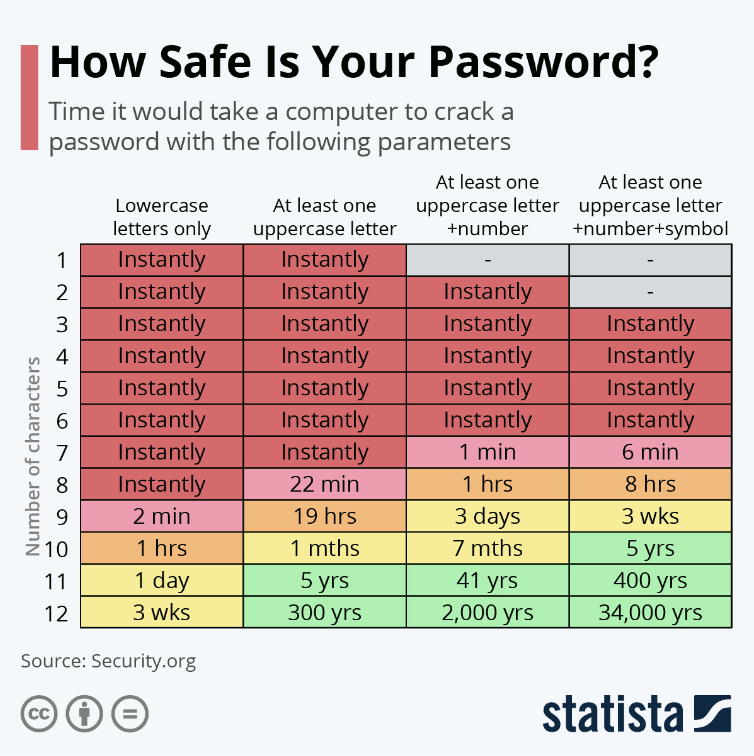
How to combat: Mandate that employees update passwords regularly and include at least 12 to 14 characters in their passwords, with a combination of uppercase letters, lowercase letters, numbers, and symbols. Make sure they avoid words from the dictionary and things like the name of your company or product. This handy chart from Statista shows how long it would take a computer to hack your password.
Method #2: Phishing Attacks and Fake Password Reset Notifications
Cyber criminals are creatively tricking unsuspecting and distracted employees to click on corrupt links that deploy malware, sabotage systems, or steal intellectual property. Common routes include email, text message, social media, or phone. Spear phishing is also a common way to dupe employees. It’s a personalized level of phishing in which the bad actor uses information about a company or fellow employee to help validate their authenticity as a trusted source.
How to combat: Educate and empower your employees to play a proactive role in your security practices. Focus on training employees to identify phishing schemes and social engineering tactics. Provide guidance on safe browsing and conduct regular phishing drills to help teams develop defensive skills.
Method #3: Stolen Passwords, Shoulder Surfing, and Hacking Phones
Many cyber criminals take the easy road by purchasing user credentials on the dark web. Password sales are big business. Hackers who break in and steal information often turn around and sell it. Another common tactic is “shoulder surfing,” which is the practice of physically viewing or recording password entry on a device screen. It is especially easy in crowded spaces, like airports and tradeshow floors, but can also be done from a distance using cameras or binoculars. Hackers often take the next step to steal the actual phone or device.
How to combat: Like phishing, the key is educating and empowering employees to be aware, always keeping their passwords secure and out of view. For any scenario where a bad actor gains password access, adopting a companywide Zero Trust posture provides the best defense to limit the attack surface. Once in your systems, cybercriminals often move across environments searching for business-critical data, confidential information, and your backup systems.
The proper access protocols prevent destruction from spreading beyond a single user or device, while gaining valuable time to isolate and combat the threat. Best practices for users, tools and machines include:
- Strong identity and access management (IAM) with multifactor authentication (MFA) and Role-based access control (RBAC)
- Biometrics
- Hardware security keys
Essentially, allow data access only to those users who truly need it.
Additionally, implement a robust policy to frequently rotate user and application passwords. Integrations with privileged-access management solutions such as CyberArk help. These ensure that passwords are constantly rotated and critical systems like backup infrastructure actively retrieve passwords only when data-protection operations are to be executed. Another helpful solution is to integrate with a SAML 2.0-based identity provider that incorporates biometric or password-less authentication mechanisms.
Method #4: Man-in-the-Middle Attack
A man-in-the-middle attack (MitM) occurs when hackers intercept a network connection and steal passwords or any other data during transmission. Examples include web session hijacking, fake WiFi networks, and DNS spoofing. Once a trusted user of computer systems connects to their privileged accounts, a "man-in-the-middle" observes every bit of network traffic, quickly compromising systems.
How to combat: Encrypt data — both in transit and at rest — for optimal data protection. If cybercriminals get your data, encryption protects it from being exploited. Other tactics include using key management service with a tamper-resistant hardware security module (HSM) and employing cryptography standards such as FIPS 140. Bring Your Own Encryption Key (BYOK) models also allow you to retain control and management of your encryption keys.
Method #5: Malicious Insider or Disgruntled Employee
Insider threats can come from current or former employees, moles, or unintentionally negligent insiders. Unfortunately, these types of attacks — especially from malicious insiders or moles —are more common as criminals become more desperate to cause disruption. Most recently, Tesla reported that a data breach affecting more than 75,000 company employees was an insider job.
How to combat: In addition to the previous, the best way to deter insider attacks is to implement a multi-person authorization model in which critical operations require the consent of more than one trusted individual.
Isn’t this Cybersecurity 101?
Some of these suggestions might seem like basic guidelines. Of course, safeguarding your data with encryption and changing passwords frequently are important steps. Yet, criminals have used these gaps to take down big enterprises over the past few years. Ride-share company Uber experienced a security breach via a previous employee’s username and password found on the dark web by a teenage hacker. And in the notorious Colonial Pipeline incident, one password shut down half the United States fuel supply in 2021.
Implement Strong Cyber Resiliency Solutions
At Veritas, we are committed to the success of every IT professional while ensuring the resilience of every enterprise from cyber threats. Our solutions extend beyond data protection and compliance, with a security mindset at the core of everything we do.
Our philosophy is to build a multi-layered cyber-resiliency approach to safeguarding your business. This strategy should include best practices around identity and access management like:
- Multi-factor authentication
- Role-based access controls
- Data encryption
- Immutable storage
- Turn-key isolated recovery environments
Veritas also provides powerful solutions like AI-powered anomaly detection and malware scanning to monitor and notify you when suspicious events occur. It is also essential to optimize environments for recovery and set up non-disruptive recovery rehearsals to limit downtime and reduce the impact of an attack. Veritas appliances add layers of security on top of software, including immutable storage with an indelible compliance clock, integrated container isolation, and a security hardened operating system.
Learn more about the cyber-resiliency solutions: Visit our cybersecurity resources or walk through our day-in-the-life of a ransomware attack experience.
