Protect your data, detect threats, and recover at scale.
Read Technical ValidationRansomware can be hugely disruptive and costly, which is why organizations of every size need a plan of action. Especially today, with ransomware as a service becoming a lucrative business for bad actors. Veritas provides a proven, multi-layered approach that ensures cyber resiliency in three key ways—complete protection across any workload and any cloud; proactive detection of anomalies and threats; and flexible, rapid, pre-rehearsed recovery.
Ransomware is the fastest growing cybersecurity threat today.
236.1 million

Ransomware attempts in the first half of 2022.1
96%

Business leaders who rank ransomware as a critical threat.2
32%

Businesses that paid a ransom and still lost over half their data.3
Veritas delivers unmatched ransomware protection and resilience.
We also deliver unmatched peace of mind.
Eliminate doubt from data protection.
Zero Trust Foundations
Built-in identity and access management, including multi-factor authentication (MFA) and role-based access control (RBAC), along with encryption for data both at rest and in-flight.
Immutable and Indelible Storage
Built-in immutability and indelibility strengthen operational and data resilience across third-party hardware, cloud-based locked object storage, and SaaS workload backups.
Data Encryption
Safeguards data at rest and in transit by providing encryption from cloud and storage provider settings. Even if cybercriminals are successful in getting to your data, having it encrypted protects it from being exploited.
Detect anomalies and malicious activity.
Total Infrastructure Visibility
Continuously monitors, detects, and mitigates potential threats and vulnerabilities with a unified view of data, infrastructure, and user activity.
Cross-System Anomaly Detection
Automatically detects unusual data and user activity across your entire infrastructure. This includes unusual write activity, known malicious file extensions, and even unusual access activity.
Malware Scanning
Locates and eliminates malware across your infrastructure with on-demand and automated malware scanning. When recovery is necessary, auto scans with clear warning prompts and spot-checking of known high-risk areas ensures recovery of only clean data.
Optimize for recovery. Be ready. Test often.
Recovery Systems
Flexible, hybrid, and rapid recovery, with the ability to automate and orchestrate complete cross-site or cross-cloud restoration—at scale, with a single click.
Non-Disruptive Recovery Rehearsals
Efficient to execute, cost-effective recovery rehearsals for all tiers of business. We enable rehearsals that are automated and assured while leveraging non-production resources such as network fencing and sandbox environments.
Eliminate doubt from data protection.
Zero Trust Foundations
Built-in identity and access management, including multi-factor authentication (MFA) and role-based access control (RBAC), along with encryption for data both at rest and in-flight.
Immutable and Indelible Storage
Built-in immutability and indelibility strengthen operational and data resilience across third-party hardware, cloud-based locked object storage, and SaaS workload backups.
Data Encryption
Safeguards data at rest and in transit by providing encryption from cloud and storage provider settings. Even if cybercriminals are successful in getting to your data, having it encrypted protects it from being exploited.
Detect anomalies and malicious activity.
Total Infrastructure Visibility
Continuously monitors, detects, and mitigates potential threats and vulnerabilities with a unified view of data, infrastructure, and user activity.
Cross-System Anomaly Detection
Automatically detects unusual data and user activity across your entire infrastructure. This includes unusual write activity, known malicious file extensions, and even unusual access activity.
Malware Scanning
Locates and eliminates malware across your infrastructure with on-demand and automated malware scanning. When recovery is necessary, auto scans with clear warning prompts and spot-checking of known high-risk areas ensures recovery of only clean data.
Optimize for recovery. Be ready. Test often.
Recovery Systems
Flexible, hybrid, and rapid recovery, with the ability to automate and orchestrate complete cross-site or cross-cloud restoration—at scale, with a single click.
Non-Disruptive Recovery Rehearsals
Efficient to execute, cost-effective recovery rehearsals for all tiers of business. We enable rehearsals that are automated and assured while leveraging non-production resources such as network fencing and sandbox environments.
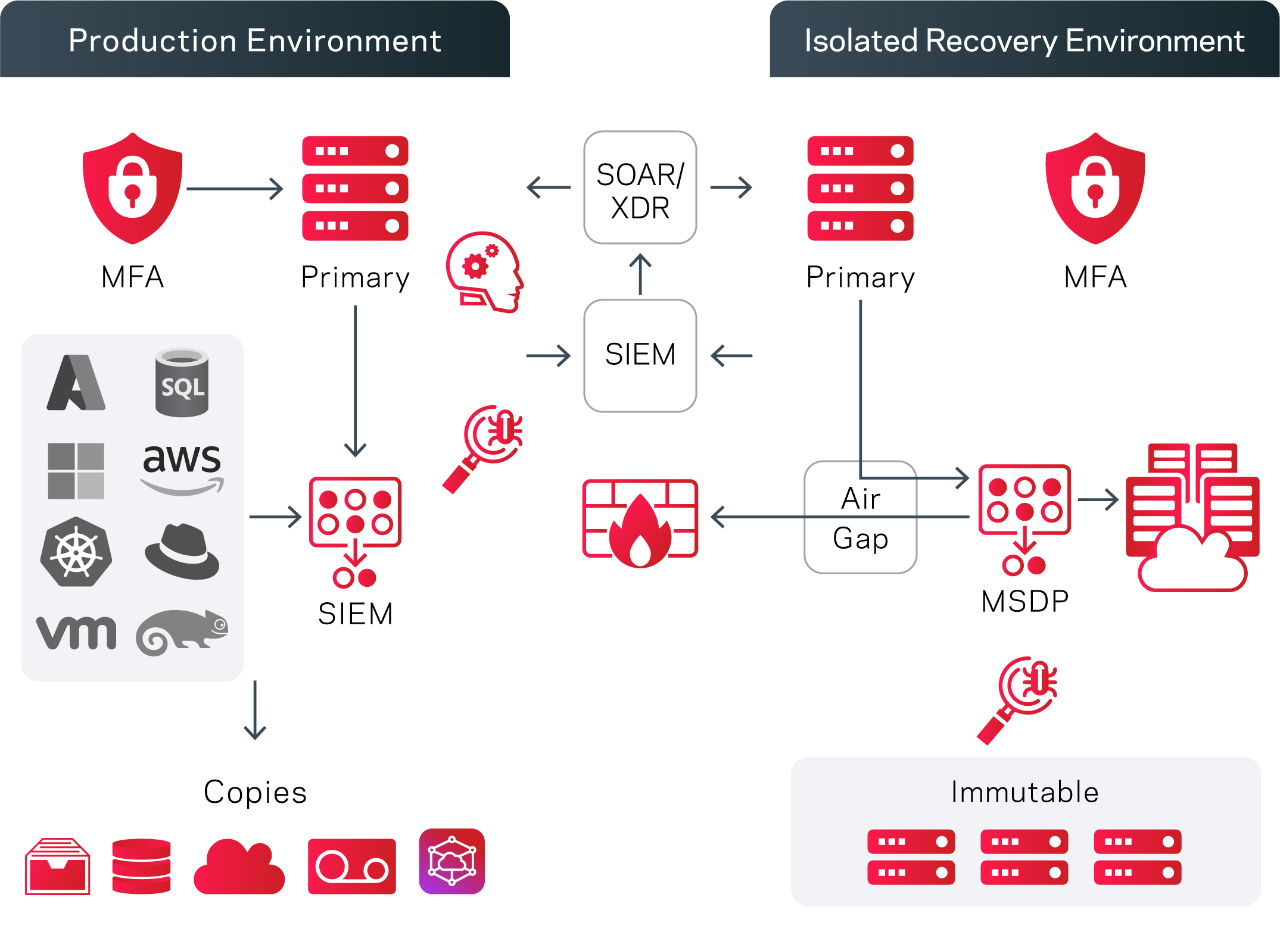
Deploy air-gapped options that other providers can’t match.
An air-gapped isolated recovery environment (IRE) can be an optimal way to ensure secure backup data for clean recovery. This environment should employ methods to do test restores of production data, perform malware scans, ensure that any discovered infections cannot spread, and perform data forensics as needed. Veritas has you covered with our industry-leading NetBackup for on-premises, and Veritas Alta™ Data Protection for the cloud.

Optimize ransomware protection for SaaS data and applications.
Veritas solutions are proven to deliver recovery of business-critical SaaS data with near-zero RPOs (recovery point objectives) and RTOs (recovery time objectives). By leveraging the power of Veritas Alta™ SaaS Protection, your organization can simplify data management and protection with a single, fully managed, backup as a service solution. Capabilities include: end-to-end encryption, granular role-based access control (RBAC), SOC compliance, and flexible account hosting.

Proud to be named a Leader in the 2024 Gartner® Magic Quadrant™.
19x a Leader for Enterprise Backup and Recovery Software Solutions.
Protect against ransomware at the edge with purpose-built appliances.
With edge computing comes security vulnerabilities, as IoT devices are notoriously insecure. NetBackup Appliances bring together the power of NetBackup software with state-of-the-art servers and storage technology to enable fast deployment of enterprise-class ransomware protection that is proven resilient at the edge. With complete lifecycle support that begins at installation, NetBackup Appliances simplify enterprise data management and protection across every environment while keeping costs down.
Get resilient against ransomware with our industry-leading products.
In every circumstance we’ve faced, NetBackup has delivered the protection we’ve required. This was particularly crucial when we experienced a ransomware attack on our unstructured data. Without NetBackup, we could not have fully recovered on any timeline, which would have caused significant problems for our business. But because we had all the data in Veritas NetBackup, we were able to completely recover from the attack in just six hours.

