Cyber Security as a Team Sport

As your organization's data and infrastructure continue to evolve and become more complex, there is an even greater need for collaboration among all teams involved in information security. Especially during the transition from on-prem data centers to a more distributed environment across edge and public cloud providers. Ransomware is becoming more prevalent. The total cost of a data breach continues to increase with an average cost of $4.45 million (USD). To mitigate the growing threat, we have to work together and build toward resiliency.
Modern security teams are organized around deep sub-disciplines, with different toolchains and expertise. You might have heard of, or currently work within, the two main cyber security groups: Red Team and Blue Team:
- The Red Team focuses on offensive security and consists of employees or contractors who act as ethical hackers, finding security vulnerabilities that malicious individuals could exploit.
- The Blue Team focuses on defensive security, implementing protective measures within your organization.
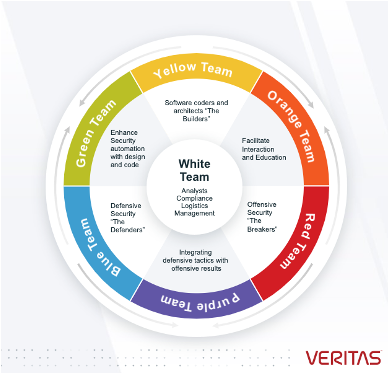
Check out this helpful article for more details on how each team operates.
With the challenges of skills gap and budgets, let’s all admit some of you wear each of these colors for a few hours or minutes every day. It might feel like you are on Team Rainbow. If you feel overwhelmed and wish you had another teammate to share your job, I would love to introduce you to a new colleague.
"New" Cyber Security Team Member
Across all these disciplines and colorful security teams, one discipline is not always top of mind when you think about data security. Given that this post is from Veritas—a trusted provider of data protection—you might have guessed that the "new" team member is a backup and recovery admin.
They move all your most important data across your network daily, protecting everything from data, workloads, and databases to network storage, operating systems, and virtualized servers. In order to move all that data across the network every day, these people often know far more about your network then you might expect. They’re aware of what networks are connected or not and how much time it takes to restore a non-trivial data set.
Why do I consider backup and recovery admins to be a new member of the team? The answer is right in the NIST Framework: Recovery. Ultimately, if the security team needs to Respond to a large-scale incident, you’ll need to Recover from your backup copies. If you want to be ready for that day, the security teams need to practice and work out how they’ll collaborate effectively to ensure you get the data back and you never re-infect yourself.
Backup and Recovery Is a Component of Cybersecurity
Unfortunately, it is never as simple as “do you have a backup?” You must factor in recovery goals, such as recovery point objectives (RPOs) and recovery time objectives (RTOs).
- RPOs refer to how much data you can bear to lose. Depending on your risk tolerance, you can set up retention policies as one copy backed up 12 times a day, every day, week, or month. This way, you can get everything before the backup date if you need to recover. If you follow the 3-2-1 backup strategy, you have at least two copies (in addition to the original) in two locations (for example, on-prem and cloud or in two different data centers).
- Once you have enough recovery points to satisfy the risk of data loss, you need to consider RTOs. These refer to how long an outage you can tolerate, specifically the time it will take from the point you decide to restore the data and the point at which all the data has been moved back. No matter how fast your network is, data has gravity. It takes time to move it from point A to B depending on how you stored the backup data and the speed of the receiving system to write the data.
Now that I’ve given you an introduction into a few important TLAs about your new friends in data protection, let’s talk about an intersection point between Backup and Recover and the Security teams.
Modern backup strategy requires malware and anomaly scanning. If you are new to backup, this might be surprising. The backup was probably clean on the day of the backup. After all, a malware scanner or threat-detection technology was in place on your server where the data originated. Realize that a backup is like a time machine for data. Over time, malware heuristics or signatures change, which means you may have infected data in your backup system. Don’t worry, Veritas keeps that data in a 100% inert form so it can’t wake up and infect your systems. However, you must ensure that your live data is free from malware and vulnerabilities for recovery. We do that automatically for you. We can also use indicators from the backup infrastructure, like anomalies we see in the data or actual malware scans to inform SOC operators by integrating NetBackup with a SIEM/SOAR solution.
Working Together
Bringing everything together, you can now build a cyber resiliency team that can not only Protect (Blue Team) and Detect (Red Team) but also Recover. There is a lot to unpack regarding Business Resiliency Fundamentals.
If you take nothing else away from this conversation, it’s this: Bring all your security-minded team members to the table and test, test, and retest your cyber resiliency and recovery orchestration.
With Veritas as one of your team members, you can rehearse and restore to a sandbox environment without impacting the production environment. One of the reasons organizations are so terrible at testing disaster recovery plans is that they're disruptive to production. The best results for orchestrated recovery let you rehearse repeatedly and continuously improve your cyber resiliency.
Learn more about Veritas’s approach to disaster recovery and invite your backup admin to your next tabletop simulation.
