Cloud is the #1 ransomware attack vector for cybercriminals.
When it comes to managing and protecting enterprise data in the cloud, there are many vectors that leave organizations vulnerable to attack and disruption. Uncertainty around the shared responsibility model, poor visibility across applications and workloads, and an overall lack of a zero trust mindset all contribute to their risk exposure. Veritas provides a multi-layered data security strategy that safeguards your cloud data — anywhere and everywhere.
Veritas can help you manage your data security with confidence.
Reduce Risk
Safeguard your data across every cloud environment.
Eliminate Uncertainty

Monitor all data, detect anomalies, and mitigate threats.
Maintain Control

Ensure performance, availability, and cross-cloud mobility.
Optimize the resilience of all your data across every cloud model.
Veritas solutions provide a set of unified IT services to enable your business to be highly available and agile—region to region, cloud to cloud, and even cloud to on-prem.
- Engineered with zero trust fundamentals and data security best practices at the core.
- Strict identity and access management such as multi-factor authentication and role-based access control (RBAC) are standard, supporting configurable authentication strengths.
- Data encryption, immutable storage, and solution hardening keep cloud data secure and minimize attack impact.


Build the best defense against cyber threats.
Data Encryption At Rest and In-Transit
As a premium storage provider, Veritas offers powerful encryption for optimal data protection. If cybercriminals are successful in getting to your data, having it encrypted protects it from being exploited.
Autonomous Data Management (ADM)
By combining automation with advanced AI and cloud learning, ADM intuitively adapts and corrects, improves business resiliency, ensures efficient operations, actively defends against cyber threats, and reduces the cloud carbon footprint.
Immutable and Indelible Storage
Veritas provides extra safeguards against ransomware, with immutable and indelible storage. This ensures that data cannot be changed, encrypted, or deleted, preventing data tampering and unauthorized access.
Isolated Recovery Environment (IRE)
To ensure a secure backup for clean recovery, Veritas offers an Isolated Recovery Environment with an air gap solution. Run test restores of production data, perform malware scans, prevent infections from spreading, and (in some cases) perform data forensics. This provides administrators a clean set of files on demand to neutralize the impact from a ransomware attack.
SaaS Data Protection
Veritas provides a unified data management and protection solution delivering a single, fully managed, cost-effective platform for SaaS workloads (including Microsoft 365). Find out more about Veritas Alta™ SaaS Protection.
Flexible, rapid recovery across on-prem, hybrid cloud, and multi-cloud environments.
White Paper: Isolated Recovery Environment (IRE)
White Paper: Isolated Recovery Environment (IRE)
Build a multi-layer fortress to protect your data.
Read White Paper
Veritas Alta™ Recovery Vault
Fully managed, cloud-based data retention for disaster recovery at scale.
See Product DetailsEliminate uncertainty in your data environment.
Avoid creating data management silos or exposing critical data and systems to unnecessary risks. Veritas exceeds data protection and resiliency standards imposed by security-aware, multi-cloud organizations across the globe.
AI-Powered Anomaly Detection
- Stay on top of any issue as it arises, with cross-cloud anomaly detection that detects out-of-the-ordinary data and user activity across your environment.
- Get alerts about suspicious anomalies in near real-time.
Cross-Cloud Data Visibility
- Gain comprehensive insights with alerts and reports correlated across your entire data infrastructure.
- Make informed decisions in the face of a cyber-attack with reporting options that help you gain visibility into your backup environment.
- Identify potential false positives and anomalies by comparing historical backups against the new backup with NetBackup IT Analytics.
Proactive Malware Scanning
- Detect multiple types of malware such as the encrypting type and the exfiltration type, providing automated and on-demand scans.
- Remove human dependencies and allow artificial intelligence/machine learning (AI/ML) technology to scan for malware.

Implementing zero trust architecture along with immutable and indelible storage, and malware scanning techniques within the IRE further secures backup data from the risks of malware and ransomware.
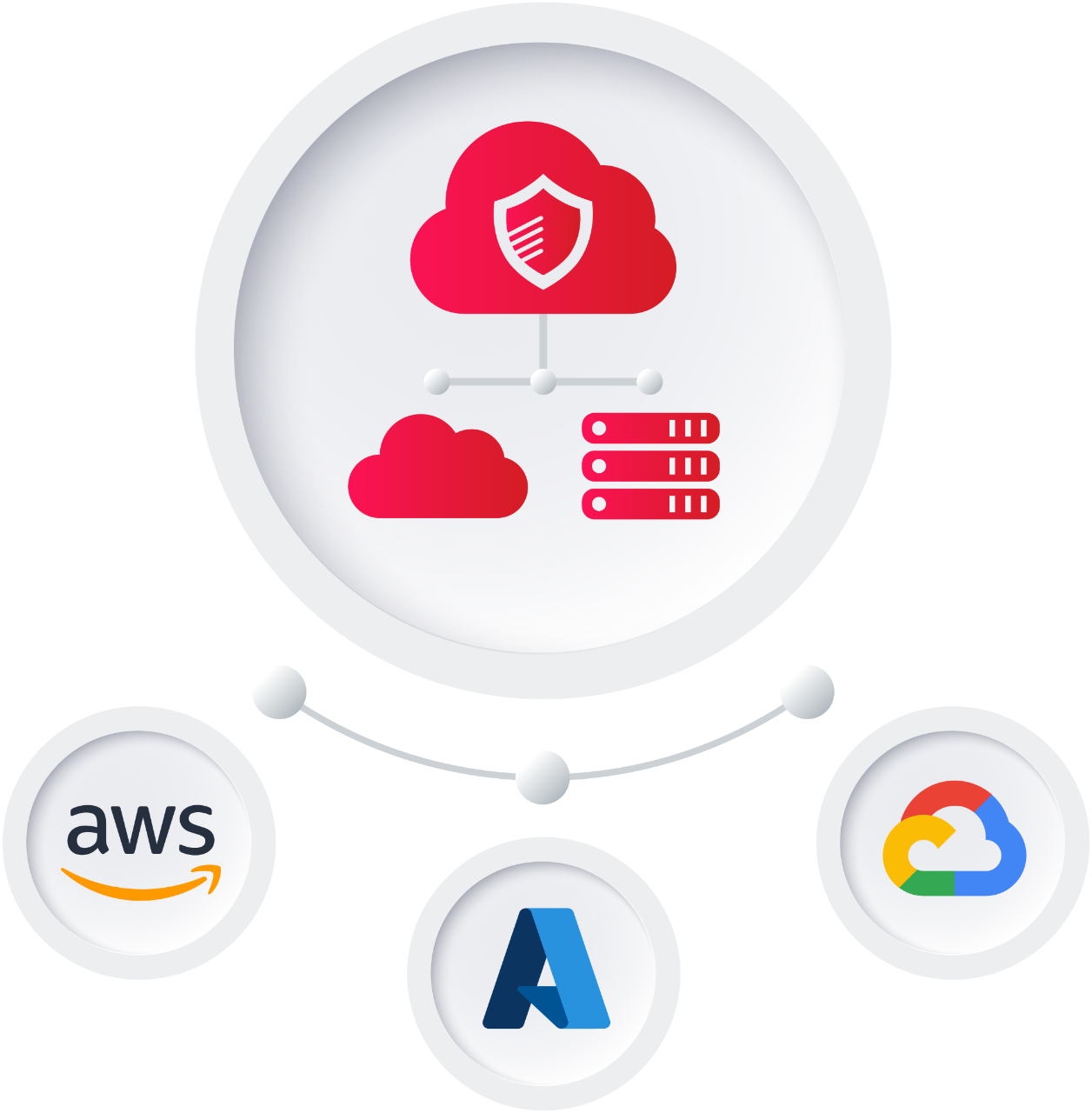
Gain control of your applications and multi-cloud data security.
Avoid cloud service provider lock-in, maintain better resiliency, and protect against cloud provider outages. With Veritas, moving your applications within public and hybrid cloud architectures is easy.
- A holistic cloud solution that delivers resiliency, protection, and management for AWS, Azure, and Google Cloud, alongside the traditional data center.
- Ensures that any uptime service-level agreement is achievable — not just region to region, but cloud to cloud, or even cloud to on-prem.
- Simplifies the complexity between applications and platforms to create common IT services that enable your business to be highly available and agile.

