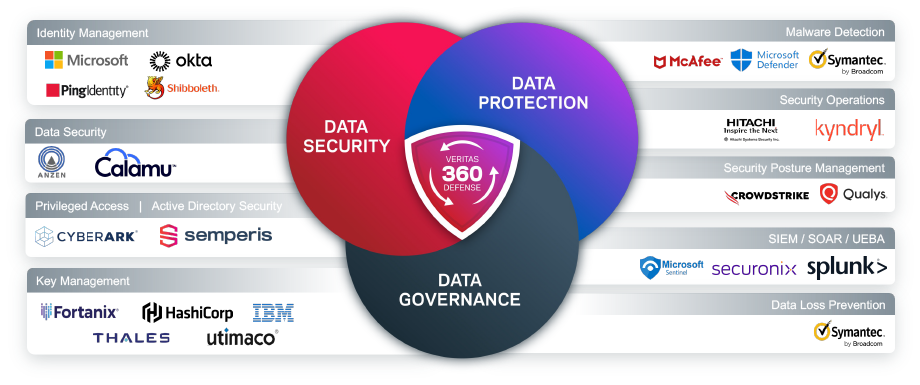
Veritas Cyber Strategy—Expanding Ecosystem

Last fall, Veritas introduced Veritas 360 Defense architecture, which uniquely combines data protection, data security, and data governance with an ecosystem of partners. With Veritas 360 Defense, we highlighted our Secure by Design and Secure by Default solutions that provide complete control across your data infrastructure. Since security is a team sport, we integrate with our Veritas 360 Defense security ecosystem partners to interoperate and augment your existing solutions.
Today, we announced partner ecosystem expansion with fantastic new integrations with your existing tools and processes so you can secure your business and prepare for a confident cyber recovery. By leveraging existing security solutions and processes you already have, you can eliminate silos that exist between IT, security, and governance teams to ensure a more resilient security posture across your infrastructure and automate incident monitoring and responses.
HashiCorp
Veritas REDLab Validation
In the Veritas REDLab, we constantly test our products with malware and the latest mass deletion and encryption tools. Last fall, we announced that Microsoft became the first Veritas 360 Defense partner to achieve Veritas REDLab Validation for Microsoft Defender. Today, HashiCorp became our next partner to achieve Veritas REDLab Validation for their key management capabilities.
HashiCorp is a leader in Encryption Key Management Software. Centrally managing and protecting your encryption keys ensures you can meet governance standards, rotate and distribute keys in a scheduled or on-demand fashion and ensure your data is unreadable to unauthorized parties. Together, HashiCorp and Veritas ensure encryption of data at rest, either on tape, disk, or in the cloud, to prevent theft of data.
Securonix
Leverage Veritas and Securonix to provide insights on user behavior in Veritas NetBackup data protection. With Securonix, security operations can monitor NetBackup user activity logs to detect actions or patterns that indicate account compromise, malicious insiders, or privileged account abuse. With continuous user activity monitoring, organizations can improve the security and reliability of disaster and cyber recovery.
I spoke with Mark Stevens, Global VP and leader of Channels and Alliances at Securonix. We explored how Veritas and Securonix use integration and AI to help our joint customers see the bigger picture and fend off this newly prevalent form of human-centric attack. We also discussed the sobering statistics from Securonix’s Insider Threat Report, including the fact that 25% of organizations have had six or more breaches last year.
Anzen Technology Systems
Numerous organizations across various industries handle exceptionally sensitive or classified data at rest—data stored, backed up, and archived. Anzen's enhanced data security and advanced encryption can thwart 'Harvest Now, Decrypt Later' attacks, and with data sharding, it is mathematically impossible to reconstruct the original data without possessing all data fragments. These fragments can be dispersed across geographically distinct locations and/or cloud platforms, each requiring authorized access and fortified with its own security measures.
Calamu
Calamu uses sharding and redundancy to ensure data availability, even during an attack, by creating a Calamu data harbor. Backup data stored in a data harbor can completely self-heal from a ransomware attack with zero downtime and no threat of data theft. Their solution includes cloud and on-premises options and attempted compromise alerting to give even the largest institutions the confidence to move data operations into the cloud.
Splunk
Leverage Veritas and Splunk to provide insights on user behavior from audit information from Veritas NetBackup data protection. With Splunk User Behavior Analytics (UBA), security operations can monitor NetBackup user activity logs to detect actions or patterns that indicate account compromise, malicious insiders, or privileged account abuse. With continuous user activity monitoring, organizations can improve the security and reliability of disaster and cyber recovery.
Semperis
While Semperis was included in our initial Veritas 360 Defense announcement last year, we have been worked together to expand the integration and better support customers’ security posture.
Semperis attack path management helps you identify and close the paths attackers use to target data protection solutions:
- See risky access, remove excessive privileges, and create secure zones for authorized privileged groups.
- Get real-time notifications when an authorized user attempts to join a privileged group with access to Veritas storage.
- Continuously monitor the identity system for unwanted changes and automatically remediate risky settings to improve overall security posture and block unwanted access to sensitive business data.
OCSF
Alongside our growing ecosystem of partners helping the Veritas 360 Defense scale, our engineering team has also been working on integrating with a broader set of tools and applications through OCSF. The Open Cybersecurity Schema Framework is an open-source project delivering an extensible framework for developing schemas. This means that if any of your existing security tools use OCSF, Veritas can strongly integrate through industry standard user and event logging. This will allow your team to connect the dots more easily across your infrastructure through a standard format.
OCSF integration is just one of the many ways Veritas ensures our solutions are tested to meet industry standards and certifications, including DoD STIG, NIST 800-53/37/171, FIPS validation, CMMC, IPv6TLS 1.3, ISO Common Criteria, SOC2, IRAP and FedRAMP Ready for SaaS Protection, as well as testing in our isolated REDLab environment.
Veritas 360 Defense
Protecting your organization’s data and applications can feel like a daunting task. With the Veritas hybrid, multi-cloud platform and our ecosystem of partners, you can manage and protect across all workloads and environments with Zero Doubt.

Learn more about the Veritas 360 Defense and the companies in our security and technology partner ecosystem during our Achieving Cyber Resilience with Zero Doubt Broadcast.
