Let’s make Cybersecurity Awareness Month extend all year long!

What a year it has been! Last year when I wrote this blog, “It should be Cybersecurity Awareness Month—every month!” I shared that cybersecurity threats were growing exponentially and only going to get worse. But as I reflect on this past year, I am so shocked! It is a crisis far worse than I could have imagined. This year has bought us large numbers of massive hacks, data breaches, digital scams, zero-day exploits, cyber warfare, malicious insiders, and ironically, a wave of hackers for “good” or for sport.
What an interesting year it has been.
Here are some harsh facts. According to SonicWall, in 2021, there were 19 ransomware attacks every second; that’s 623.3 million attacks globally. There were 2.8 billion malware attacks in the first half of 2022, and a sharp rise in “Never-Before-Seen” malware, encrypted threats, and cryptojacking. Tech Target confirmed that ransomware attacks continue to wreak havoc in new ways with an increase in Supply chain attacks, up 300% since last year, attacks on critical infrastructure, and hospitals and the appearance on the scene of double and triple extortion attack techniques. So, we know for sure cybercriminals are getting more creative.
What this now means for all of us?
Cyber security is now everyone’s concern. It is always a great time for a little best practices refresher. Here are my top six:
1. Illuminate all your Data with Data Visibility Tools
Do you know where all your data is? Yes, even at the edge? Attackers are looking for the weakest areas—those dark places where you may have limited security or oversight. That’s why it is vital to implement tools that provide full infrastructure awareness, shining a light on all those dark areas, or dark data, in your environment.
2. Protect All Data, From All Sources
Once you know where your data is, then safeguard and protect all your data, in all parts of your environment—from physical and virtual to the cloud and containers.
- Zero Trust Rules! Adopting a companywide Zero Trust posture has been proven to reduce the risk of a devastating attack. Further, if a breach happens, it reduces the attack surface or the blast radius because it provides multiple layers of security that minimize impact. For example, once in your systems, cybercriminals often move across your environment searching for business-critical data, confidential information, and backup systems. Strengthening your identity and access management (IAM) with multifactor authentication (MFA) and role-based access control (RBAC) for users, tools, and machines will limit access to highly sensitive data and backups. Only users that need to access the data should be allowed. Remember to include this on all company accounts too, especially service or social media accounts. Prevent access to these areas with strong IAM controls, privilege controls, hardening, and secure hardware all built on Zero Trust.
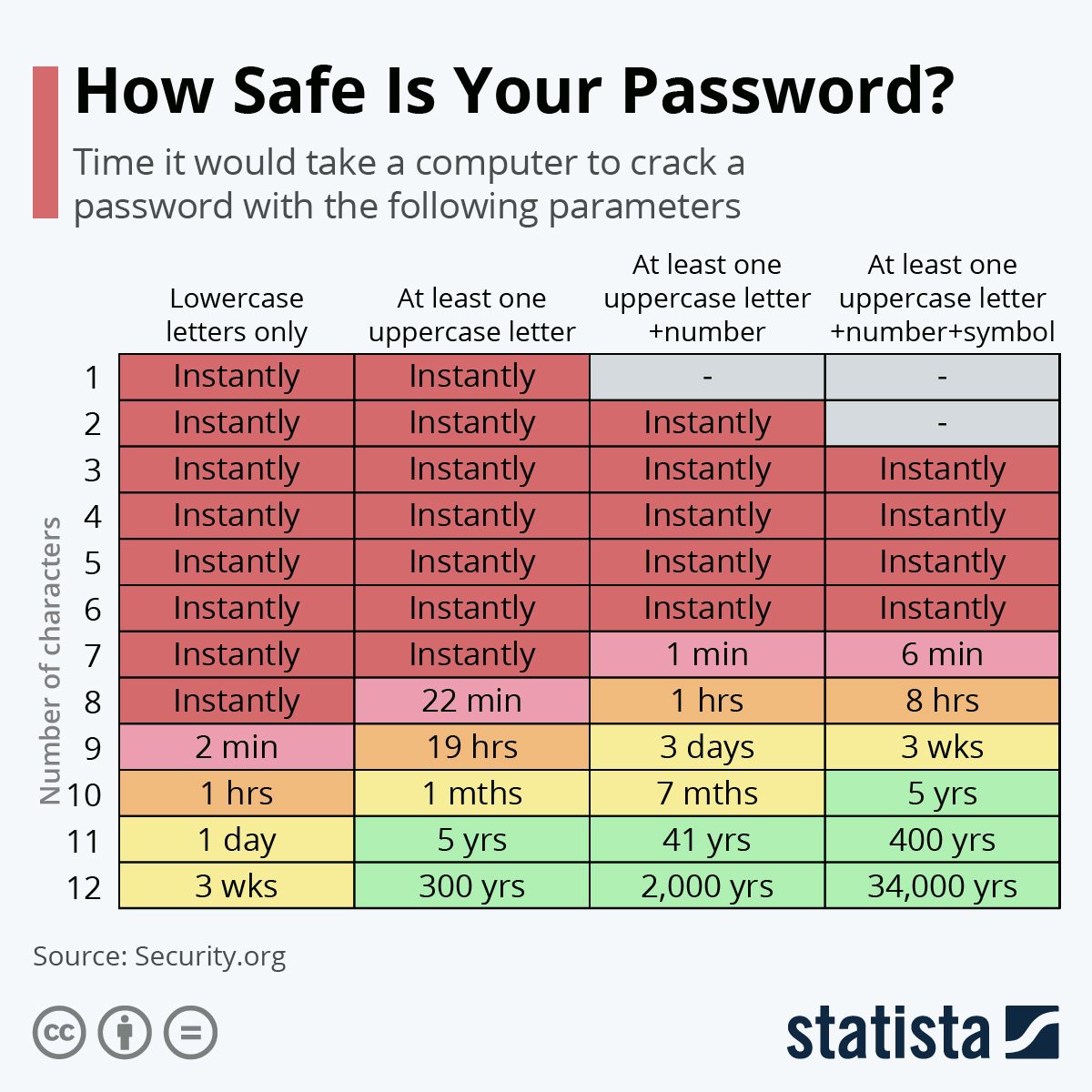
- Up your PW game! Friendly reminder that password hygiene is a top priority, no more password1234 or pizza321 etc.. those all need to retire! Never use factory passwords. Make sure your passwords include at least 12 – 14 characters with a combination of uppercase letters, lowercase letters, numbers, and symbols. Try to avoid words from the dictionary or something obvious like the name of your company, employee, or product. I enjoy this handy visual chart from Statista that shows how long it would take a computer to hack your password. Also a great visual to share widely in your personal life with your parents and grandparents. It brings the message home nicely!
- Encrypt data—in transit and at rest. As a premium storage provider, Veritas offers encryption on storage for optimal data protection. If cybercriminals get your data, encryption protects it from being exploited.
Now, you might be thinking that this advice is cybersecurity 101. Of course protecting your data and changing your passwords are important but this year alone we have witnessed simple mistakes take down big corporations. Just last month, we learned the ride share company, Uber, experienced a security breach by a teenage hacker because a username and password for a previous employee was available on the dark web. Read more about Why You Should be Worried About Uber’s Security Breach.
You can’t just assume you are safe if you have VPN, multifactor authentication, anomaly detection, and security training in place. You need to go a few steps further.
3. Implement Immutable and Indelible Storage
Implement immutable storage and network isolation using an air gap solution. One of the best ways to safeguard your data against ransomware is to implement immutable and indelible storage with an internally managed compliance clock, and set up an isolated recovery environment (IRE). Immutable and indelible storage, which ensures that data cannot be changed, encrypted, or deleted for a determined length of time (or at all) prevents data tampering and unauthorized access. Isolated recovery environments and air gap solutions isolate data, logically or physically, to help ensure that data is segmented away from the rest of the environment.
4. Adopt Data Monitoring with Anomalous Activity Detection and Malware Scanning
Implement tools that detect, ideally monitoring for abnormal behaviors and mitigate malicious activity of both data and user activity. Essentially, it is vital to implement concrete and automated measures to alert if anything happens out of the ordinary in your ecosystem. This could include anomalies such as unusual file write activity, which could indicate infiltration; but it could also include detecting known ransomware file extensions, file access patterns, traffic paths, or even an unusual jump in activity compared to typical patterns. Being notified immediately of anything out of the ordinary provides a valuable advantage to act or mitigate quickly. Additionally, these tools can help to regularly conduct cyber threat hunts.
5. Optimize for Rapid Recovery
The best defense is to ensure recovery is always an option, with flexible, hybrid, and rapid recovery that can be performed in minutes, even at scale. This is achieved by having as many recovery options as possible, including alternative recovery sites such as secondary data centers, or even standing up an entirely new data center in the cloud on demand.
6. Rehearse and Test
Cybercriminals hope that your organization, like most, is not optimized for recovery. They want maximum damage and downtime to ensure payment of ransoms. If you are ready and rehearsed for recovery, then you’re already a huge step ahead. To get to rapid recovery, you must have a cybersecurity response plan for your entire environment that includes testing early and often. Regular rehearsals of your recovery help limit downtime and disruptions and reduce the impact of an attack. Don’t forget to test early and test often—you are only as good as your last test.
By implementing the six steps above, you have the power to combat cyber threats like ransomware and flip the tables on cybercriminals. Today, no company is safe. Please take the threat seriously and prepare!
Employees are vital too!
Additionally, as part of your regular security hygiene, include educating and empowering your employees to play a proactive role in your organization’s security practices. Focus on training employees to identify phishing and social engineering tactics, build strong passwords, browse safely, use MFA, and always use secure VPNs, never public Wi-Fi. Also, ensure all employees know what to do and who to alert if they fall victim.
Looking for more guidance here? DHS announced new cybersecurity performance goals for critical infrastructure this week. Click here to learn more.
How does Veritas help?
At Veritas, cyber security and the Zero Trust practice has been part of our corporate culture for years—a huge advantage of having been conceived while we were still part of a security company. Everything that we engineer is built on that strong security foundation.
Is your organization ready to recover from a cybersecurity attack? Click here to begin our assessment to find out.
We get it, and are here to partner with you…ready to talk? >> Request a call from us.
Click here to learn more about strengthening your organization’s resiliency with Veritas.
