Self-Defending Data Protection with Veritas

Ransomware attacks are a matter of "when," not "if". Immediately detecting and stopping these attacks is critical to preventing widespread damage to your organization. Traditional detection methods are struggling to keep up with evolving tactics, such as "off-the-land" attacks, as highlighted in CrowdStrike's 2024 Threat Report. And the cyber actors are switching tactics and not just going after the infrastructure but also targeting the IT administrators themselves and their login credentials. This is a lot to deal with.
Veritas autonomously defends the data protection infrastructure – a first-of-its-kind in the data protection industry with its Adaptive Risk Engine. Veritas also leads the charge in comprehensive anomaly detection with its patent-pending, inline real-time entropy-based ransomware detection.
Adaptive Risk Engine
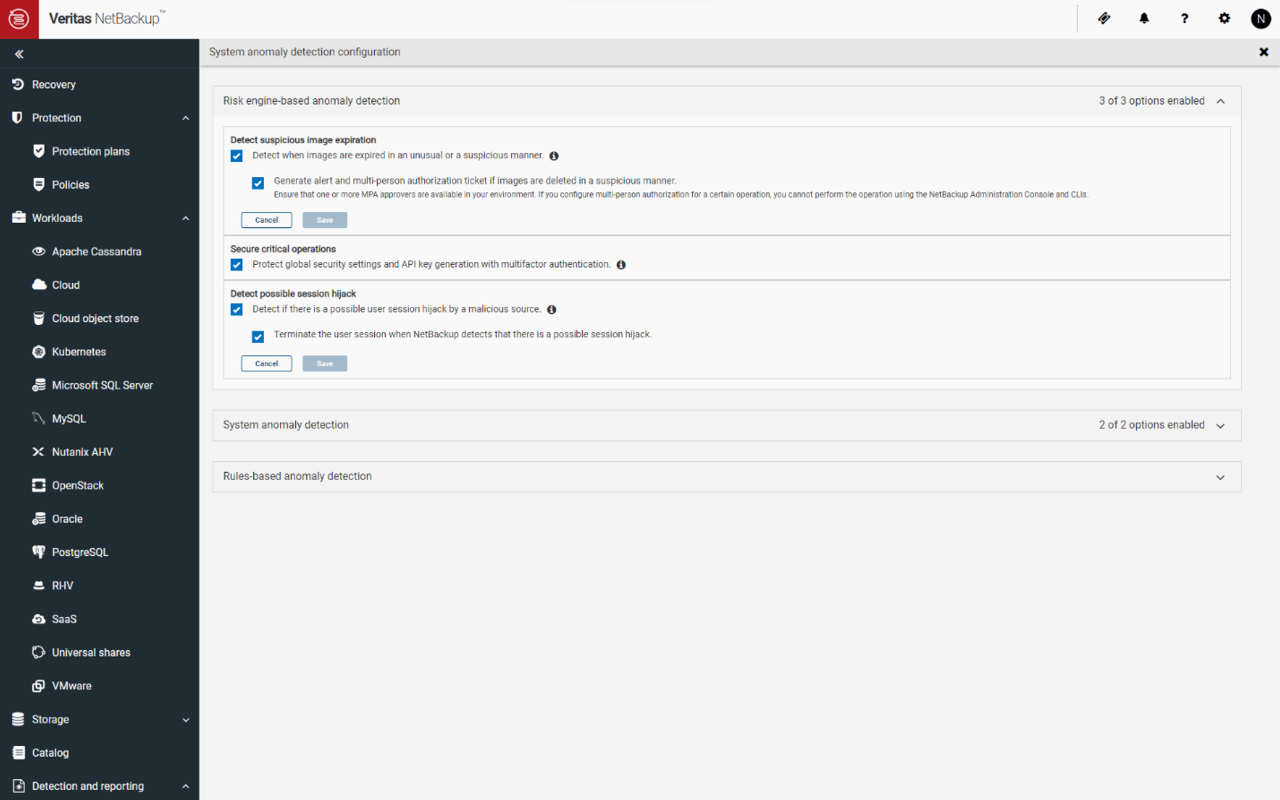
Given the increasing instances of identity theft, spoofing, and the use of deep fakes to manipulate individuals, systems must be able to detect unusual admin behaviors promptly and deploy protective measures proactively to limit data loss. The Veritas Adaptive Risk Engine addresses this challenge by tapping into user behavior models generated and continuously updated for each admin, regardless of their choice of management interface.
Today, Veritas NetBackup and Veritas Alta™ Data Protection will continuously monitor and defend themselves against threats originating from compromised admin credentials. If any unusual admin behaviors are spotted, they'll automatically deploy security measures like adaptive multifactor authentication (MFA) and adaptive multi-person authorization (MPA) to safeguard both protected data and the security of the data protection platform from cyber-attacks.
For example, a backup administrator may during operations perform a certain level of cleanup of older backups. However, if the same backup administrator’s credentials are compromised and a malicious actor begins making significant changes to policies or deleting backups, the Veritas Adaptive Risk Engine flags these actions by initiating an inline MFA prompt or an MPA request to block that action. If the MPA request is not honored within a given interval, that action is completely blocked, thus safeguarding the system. If the operation is indeed legitimate the MPA approval allows the Risk Engine to learn this new behavior.
Entropy First Approach
Traditional threat detection methods often rely on signature-based approaches, but Veritas takes a different approach, an Entropy first approach which consists of a:
Learning Phase: This phase creates stable baselines by studying backup patterns over several weeks. It continually learns specific data traits of the protected asset. This learning method, called zero-shot learning, doesn't focus on any particular ransomware type.
Action Phase: Here, the system compares live data and user patterns with what it has learned. Any anomalies are flagged for closer inspection. This zero-shot learning approach not only detects known ransomware types but also identifies new variants that weren't previously recognized.
We’ve enhanced our defense mechanisms, by prioritizing this entropy-first approach, to enable Veritas NetBackup and Veritas Alta Data Protection to detect sophisticated data attacks. Testing against a wide variety of ransomware strains in the Veritas REDLab yielded a 100% success rate with only a 0.07% false positive rate. This demonstrates that our detection strategy reliably identifies ransomware-induced encryption events.
This method significantly reduces the need for assuming specific attack details, ensuring adaptability to unexpected ransomware variations. Our patent-pending innovation allows for inline detection, ensuring identification with near-zero impact on performance during the backup process.
Enhancing Zero-Shot Learning
Veritas has upgraded its method for detecting ransomware by focusing on entropy first. This approach works better than competitors who depend on certain cloud services or delayed data scanning to catch metadata tampering. Plus, we've combined this method with zero-shot learning on multiple indicators, making our detection accuracy as high as 99.94%. In fact, in every test we conducted with different ransomware types, our model successfully detected all of them, achieving a 100% success rate.
Our zero-shot learning method relies on granular, non-linear patterns in data and metadata, all without any training specifically on ransomware. Remarkably, this model achieves exceptional efficiency in detecting ransomware strains that it had never seen before. This capability ensures robust detection against diverse attack strategies, fortifying defenses against unknown vulnerabilities and zero-day attacks.
In zero-shot learning, incorporating both amplitude and frequency dimensions significantly enhances effectiveness. Amplitude represents the strength or intensity of signals, while frequency indicates the rate of occurrence of a particular signal pattern. By considering both dimensions, the model uniquely gains a deeper understanding of the underlying data patterns, allowing it to discern subtle nuances and variations. This two-dimensional analysis enables the model to generalize better and make accurate predictions even when encountering entirely new or unseen data. In essence, leveraging amplitude and frequency dimensions empowers zero-shot learning to effectively recognize and adapt to diverse patterns, contributing to its robustness and versatility in handling various tasks and domains. Using these two dimensions enhances our ability to identify threats, minimizing false positives.
Intelligent Recovery Assistance
When Veritas detects an entropy alert, indicating possible data encryption, it swiftly initiates a meticulous recovery process. First, Veritas conducts a thorough assessment of the affected data environment to gauge the extent of the entropy change. Simultaneously, it performs real-time checks on all available backup copies to ensure their integrity and reliability, validating only secure backups for potential recovery.
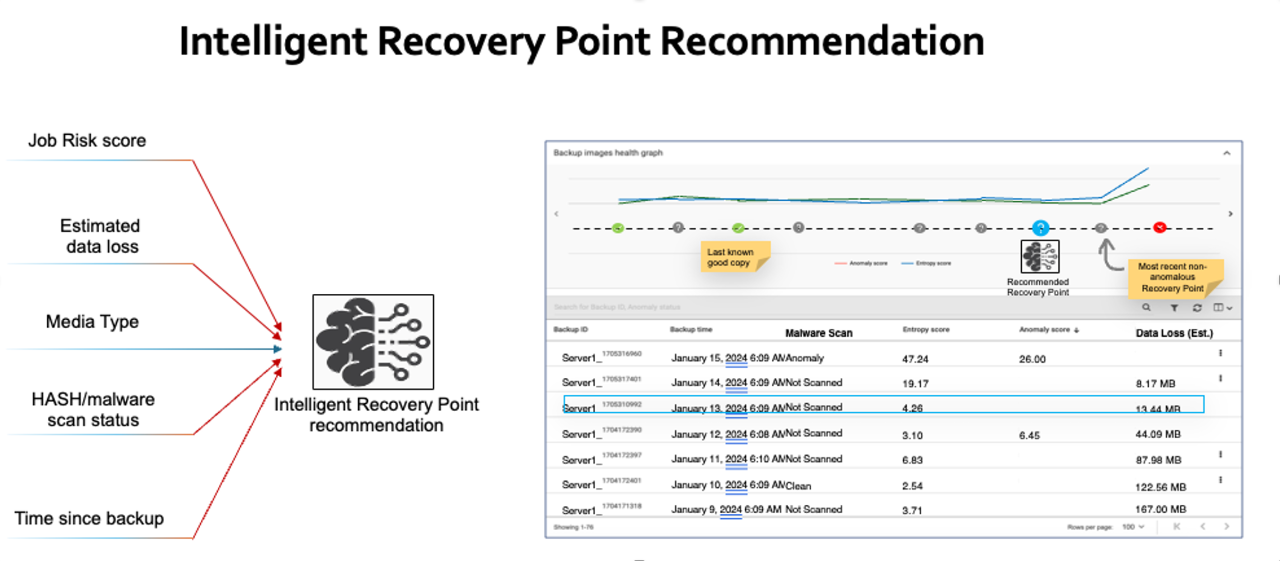
Once the validation phase is complete, Veritas leverages advanced algorithms and machine learning to identify the optimal recovery point. These algorithms consider various factors such as backup timestamps, validation frequency, and the severity of risk. By analyzing this wealth of data, Veritas determines the most recent and trustworthy backup copy that aligns with the organization's recovery goals, balancing Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs). This strategic approach not only minimizes data loss but also expedites the restoration process, empowering organizations to swiftly overcome potential disruptions identified by entropy alerts.
Veritas Patent-Pending Entropy Analysis
Feature |
Benefit |
In-line |
Immediate notification of a potentially compromised file as backup is occurring |
Zero-shot Learning |
Continuous adaptation is guaranteed through ongoing machine learning, removing the necessity for frequent model retraining |
2-Dimentional Analysis |
Strengthens our ability to discern whether the observed randomness poses an actual threat minimizing false positives |
Intelligent Recovery Assistance |
Helps rapid recovery by identifying the last good known copy that balances both the Recovery Time Objective (RTO) and Recovery Point Objective (RPO) |
Summary
Veritas has moved from zero trust to zero doubt – have zero doubt that you can quickly and effectively recover your data. With our self-defense solutions Veritas not only monitors user behavior and adjusts defenses dynamically but also uniquely identifies compromised files during data protection and aids in restoring systems to a secure, known state.
Veritas provides a robust and adaptive solution to tackle the changing landscape of ransomware threats. With its proactive approach to detection and recovery assistance, Veritas emerges as a leader in protecting digital assets from the continually increasing threat of ransomware.
For more insights on how to navigate the complexities of today's cyber threat environment with zero doubt, tune in to our virtual broadcast.
