In a world where cybercriminals no longer break in but simply log in, how do you best protect your valuable data?
We all dread the notion of our identity being stolen. The vulnerability, the unknowing, and the anxiety around who and why someone would do this. Well, imagine if that identity was the administrative credentials to your core cyber resilience solution.
With credential theft on the rise, insider-based attacks, privilege escalation, and advanced persistent threats are no longer just targeted at production or edge systems, they’re going after your last line of defense: your data protection infrastructure.
Now more than ever, data protection admins are prime targets for credential theft, due to their significant access to valuable organizational data. Assisted by AI, cyber criminals can simultaneously create more sophisticated attacks and initiate them more efficiently. Whether it’s GenAI-generated phishing schemes, using video deepfakes, or taking advantage of other new-fangled ways of impersonation, stealing or just plain convincing folks to unwittingly hand over credentials has become a favored approach whether targeting executives, other end users, or system admins.
According to a 2024 IBM report, attacks leveraging valid credentials surged by a staggering 71% year-over-year¹. This alarming trend underscores the urgent need for heightened vigilance and specialized security measures. Relying solely on enterprise-wide Single Sign-On (SSO) solutions is no longer enough. Organizations must fortify their data protection infrastructure with dedicated security controls such as Multi-Factor Authentication (MFA), Multi-Person Authorization (MPA), Privileged Access Management (PAM), and other robust defenses. Safeguarding against credential theft is paramount in defending your organization's most precious asset: its data.
A Fundamental Shift
Just a few years back, concepts like immutability, anomaly detection, and malware scanning were key focal points in hardening data protection defenses. These are now considered to be fundamental. Must haves. Table stakes even. These capabilities have forced threat actors to shift more towards going after “soft targets” by taking advantage of phishing, social engineering, MFA fatigue, and other credential-based attacks to log in, not break in, to your infrastructure.
As threat actors have evolved, so must our defense strategies. We’re at a critical juncture where the gap between the exponential growth in the value, volume, and vulnerability of data, and your teams' ability to protect and secure it is widening. The wider this gap becomes, the higher the likelihood of a major security breach, lengthy downtime, and/or data privacy compliance risks.
So how do you tackle a scenario where all your data, across the globe, is potentially impacted? How do you recover quickly and confidently after a successful cyber breach? How do you know you are recovering clean data? How do you ensure this doesn’t happen again? How do you do all this with a team increasingly staffed with IT generalists? These are some of the realities of Cyber Recovery today. Spoiler Alert: It’s a whole different ballgame compared to traditional disaster recovery.
Strengthening Cyber Resilience with New AI-Powered Solutions
Today we are unveiling a series of new capabilities designed to combat the latest round of ever-evolving cyber threats. New AI-powered product solutions include a new adaptive self-defense solution, improved entropy anomaly detection, and a new GenAI-powered operational copilot. We’re also announcing new cyber resiliency assessment and recovery services, new security ecosystem partners, and a whole lot more.
Adaptive Self-Defense Solution
We are introducing the industry's first self-defending data protection solution – an innovative and automated defense against user behavior-based ransomware attacks. Veritas NetBackup and Veritas Alta™ Data Protection now actively and continuously monitor admin user behavior and adjust defenses such as multi-factor authentication and multi-person authorization challenges dynamically when anomalies in administrative behaviors are detected. This adaptive, self-learning, self-defense solution is a first for enterprise data protection.
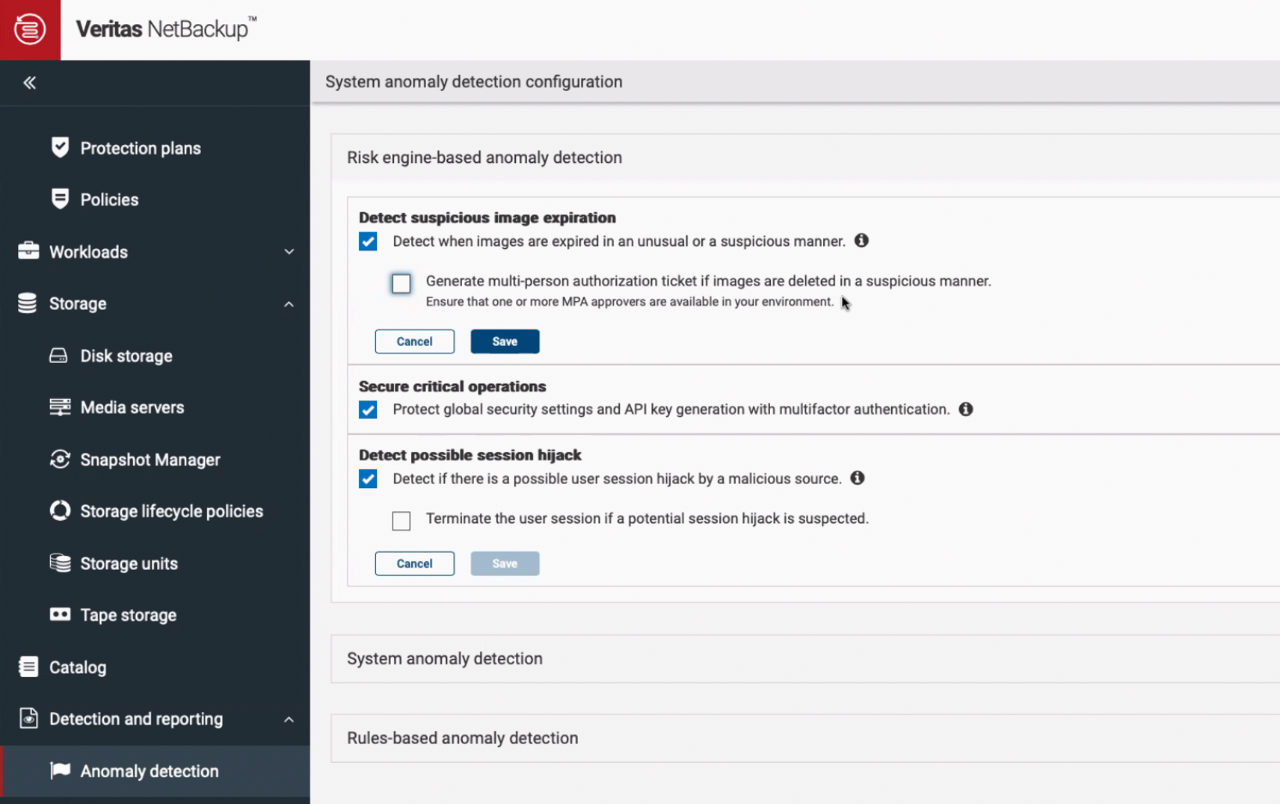
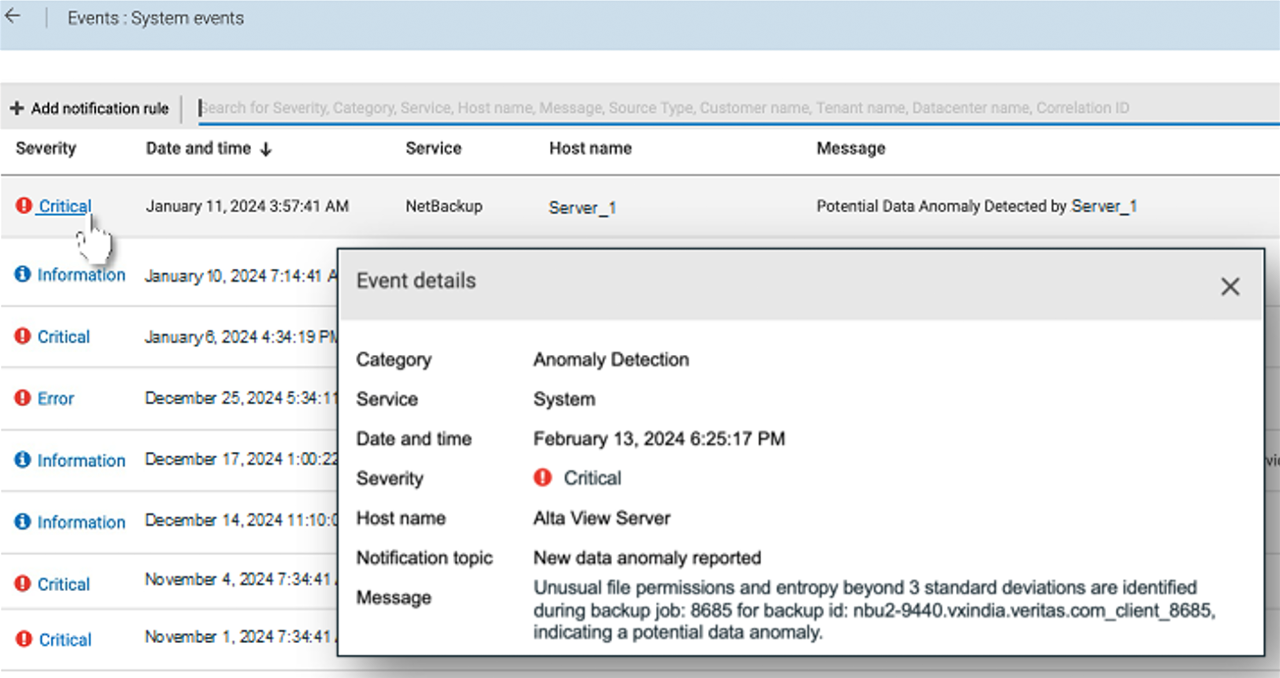
Entropy Anomaly Detection
Of course, we have been doing time series data anomaly detection for quite some time. This technique establishes stable baselines by analyzing patterns from backups over multiple weeks, while continuously learning granular data characteristics unique to the protected asset changes. This learning strategy is agnostic to any ransomware type and is referred to as zero-shot learning. What’s new is that we have made significant improvements to the way we do this: we can now detect anomalies inline as backups occur, with near-zero impact on performance while at the same time eliminating the need for additional resources or incurring expensive cloud compute costs associated with post-hoc analysis. This patent-pending innovation helps reduce the time to find and flag potential anomalies for further investigation – particularly important in limiting the potential blast radius of a breach.
AI-Powered Operational Copilot
Last but not least, we are announcing Veritas Alta™ Copilot – a GenAI-powered operational assistant designed to help data protection admins of all levels to keep up with the rapidly increasing scope and scale of their responsibilities. Veritas Alta Copilot uses Retrieval Augmented Generation (RAG) with state-of-the-art Large Language Models to provide a conversational user experience akin to having highly specialized experts on standby to help configure and protect your systems.
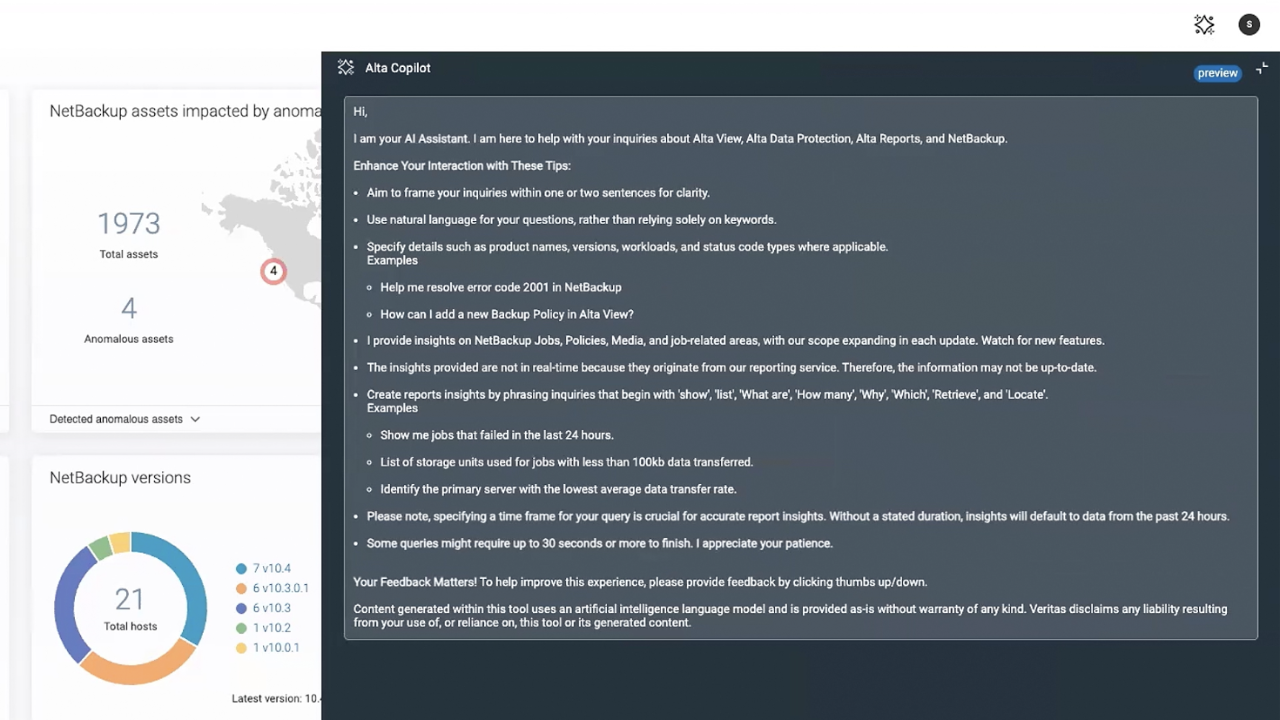
Acting as a "human assist," Veritas Alta Copilot swiftly identifies cyber vulnerabilities and operational efficiencies, recommends proactive configuration changes, and guides users through advanced data management tasks effortlessly, allowing them to extract maximum value from their technology investments.
Cyber Resilience Assessment Services
Realizing that despite all the great guidance AI can provide – sometimes our customers still want human help in augmenting their own skills, we’re introducing Veritas Cyber Resilience Assessment Services, designed to align your security practices with industry best practices in data protection and security to optimize your security posture. Through comprehensive assessments, our expert team evaluates your security practices and identifies areas for improvement. Regular assessments help to maintain a strong state of readiness, allowing you to stay ahead of emerging threats and vulnerabilities.
In the aftermath of a cyber incident, Veritas Cyber Resilience Assessment Services becomes instrumental in facilitating the restoration process. Our expert team provides immediate support to assess the extent of the damage and identify critical areas for recovery. With access to our experienced Recovery Response team, available 24/7, you receive timely assistance and guidance in restoring essential data and systems. Tailored consultation ensures a seamless transition back to normal business operations, minimizing downtime and enabling swift recovery. With Veritas, resilience isn't just a goal – it's a guarantee, even in the face of adversity.
New Security Partners
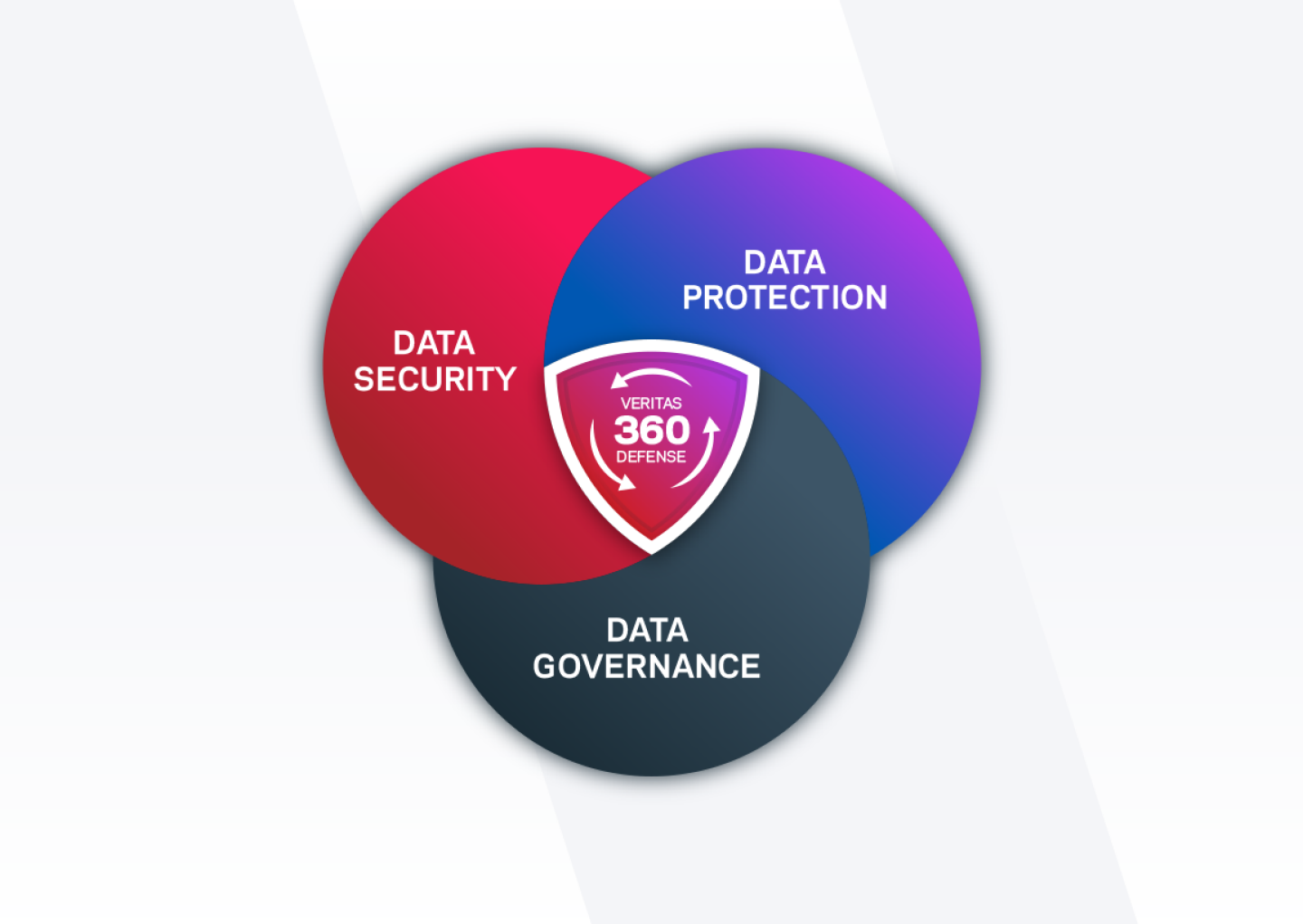
Recognizing once again that cyber-resilience is a team sport, we have expanded the Veritas 360 Defense ecosystem, adding additional security-centric partners to our ecosystem. Securonix, Splunk, HashiCorp, Anzen, and Calamu– names that resonate with authority and innovation, have now joined Veritas 360 Defense with HashiCorp completing a Veritas REDLab certification. Check out all our partners in the Veritas Trust Center.
A great example of how we are safeguarding compromised credentials is the solution we have created with Securonix. By integrating NetBackup and Veritas Alta™ Data Protection user activity logs with the Securonix UEBA platform, we’ve bolstered the defense of our data protection platform. This Collaborative effort enables us to swiftly detect potential threats through AI-driven analytics of anomalies. When suspicious activity is flagged, Securonix’s platform promptly notifies admins, empowering them to take decisive action to prevent malicious attacks.

Veritas 360 Defense
Every customer I meet faces the same challenge: creating an integrated team responsible for defending against evolving cyberattacks and recovering quickly when breaches occur. In an environment where cybercriminals no longer break in but simply log in, protecting your organization’s valuable data demands proactive, adaptive, and collaborative measures. With our latest innovations and partnerships, we’re committed to providing the tools and expertise needed to defend against the ever-evolving threat landscape, to help avoid those dreaded late-night calls and ensure zero doubt that your data is secure and quick recoveries are just a few clicks away.

For those eager to explore these innovations further, we invite you watch our virtual broadcast on-demand where we discuss the latest updates to Veritas 360 Defense and to learn more about how we enhance your cyber resilience and ensure your teams are ready for cyber recovery.

