Veritas Trust Center
Security
Safeguarding your data is our top priority.
Veritas is committed to transparency around our development practices and management of security vulnerabilities. We put security at the core of our product development, infrastructure, and processes. Read our Vulnerability Management Commitment and Disclosure policy to learn more.

A Message from Christos Tulumba, CISO at Veritas
Veritas takes security seriously and prioritizes the protection of your critical data and applications. Our comprehensive approach ensures that we address all aspects of cybersecurity to maintain a resilient environment for our customers and partners. Trust Veritas to uphold the highest standards of security and safeguard your valuable assets.
- Secure product development and testing
- Identity and access management
- Cloud security
- Endpoint protection
- User and communications security
- Vulnerability and incident management
- Secure logging and monitoring
- Security governance and risk management
- Supplier risk management
- Security culture and training
Secure Software Development
Security begins in product development, where we use secure coding methods and analysis tools. Veritas products undergo penetration testing by an independent third-party firm at least annually. Internally, our Product Security Group (PSG) conducts scans as part of the release of a new product version. In addition to managing schedules for pen testing and internal vulnerability scans, PSG also maintains the Veritas Application Security Assurance Program (ASAP) to ensure each product follows a secure development lifecycle.
The Veritas Secure Software Development Framework and ASAP program are modeled after NIST SP 800-218, a core set of software development practices focused on mitigating vulnerabilities.
Veritas aligns to the National Institute of Standards and Technology (NIST) framework—a standard that addresses cyber resiliency as five key pillars: Identify, Protect, Detect, Respond, and Recover.

Development Principles
Our products adhere to two of the core principles recommended by the Cybersecurity and Infrastructure Security Agency, National Security Agency, Federal Bureau of Investigation, and multiple international security agencies.
Secure by Design
We design and build products in a way that reasonably protects against malicious cyber actors gaining access to data.
Secure by Default
Our products are resilient against prevalent exploitation techniques out of the box without additional charge.
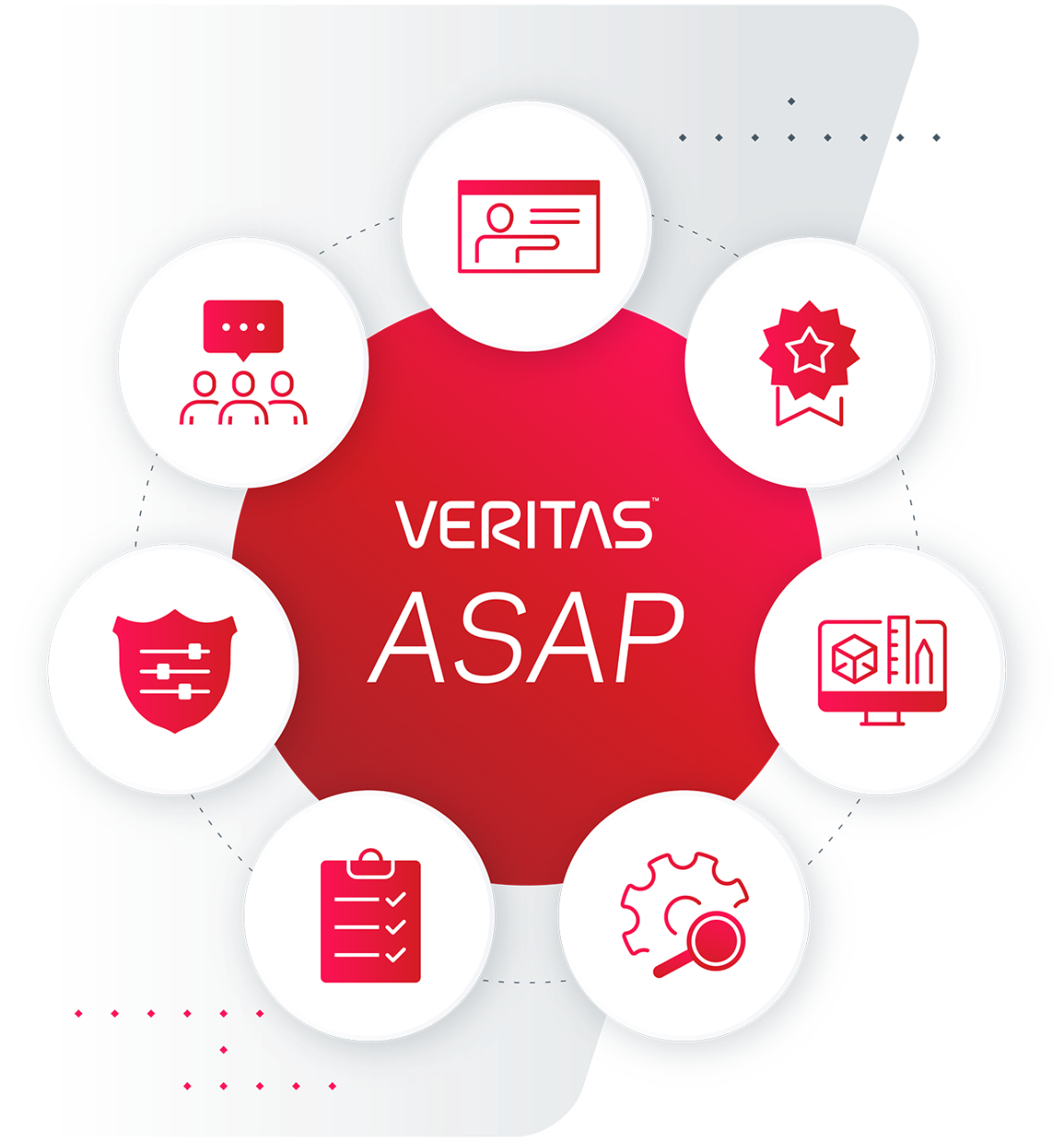
Veritas Application Security Assurance Program (ASAP)
Based on the Microsoft Secure Development Lifecycle, Veritas ASAP addresses real-world challenges and the requirements of U.S. Presidential Executive Order 14028. Our program uses automated security tools and manual techniques to identify product vulnerabilities per the executive order and CISA requirements. We score the severity of vulnerabilities using the industry-standard Common Vulnerability Scoring System to guide the urgency of remediation and public notifications.
Veritas ASAP includes seven pillars:
- Training: Product development teams undergo various security training courses to ensure they are up to date on the latest threats and mitigation techniques.
- Requirements: Validation that our products adhere to security standards, regulations, and best practices.
- Design: Ensures secure design principles are met and assesses if product has undergone threat modeling to identify potential security risks and vulnerabilities.
- Implementation: Ensures product code reviews are conducted accurately and any issues identified have been addressed.
- Verification: The product undergoes rigorous security testing.
- Deployment: Validates that each product team enforces secure configuration management practices.
- Operations: Validates that each product team has an established incident response plan, including procedures for handling security incidents, incident reporting, and communication channels.

Veritas REDLab
Veritas REDLab is a fully isolated, in-house security lab where we proactively conduct real-world testing of our software against the latest threats to validate our cyber resiliency capabilities.
Technical Alliance Partner Integration
Data security is a team sport—no single product addresses all aspects of security requirements. At Veritas, we partner with the best across the industry to optimize your investment by ensuring our products not only integrate well, but also stand up to cyber attacks. Through these strategic partnerships, we deliver industry-leading solutions across a range of areas, including:
- Antivirus
- Authentication
- Encryption
- Key Management Systems (KMS)
- Immutable storage
- Privileged Access Manager (PAM) solutions
- Security Information and Event Management (SIEM)
- Security Orchestration, Automation, and Response (SOAR)
- Extended Detection and Response (XDR)


