Cyber Recovery Isn’t Typical Disaster Recovery

Unfortunately, there is no “easy button” for recovery from a cyber attack. Nor is there a magical “restore everything” menu option. As a proactive leader, it is crucial to understand that cyber recovery is more involved than typical disaster recovery. It requires advanced planning with collaboration across internal security teams. Your list of considerations includes:
- Containment to stop access
- Forensics to understand the attacker’s entry point
- Assessment to find impacted systems
- Data decontamination to ensure you don’t reintroduce threats during recovery
Effective recovery from a cyber incident requires a holistic approach across IT disciplines including security, business continuity, and traditional infrastructure services, including the backup and recovery.
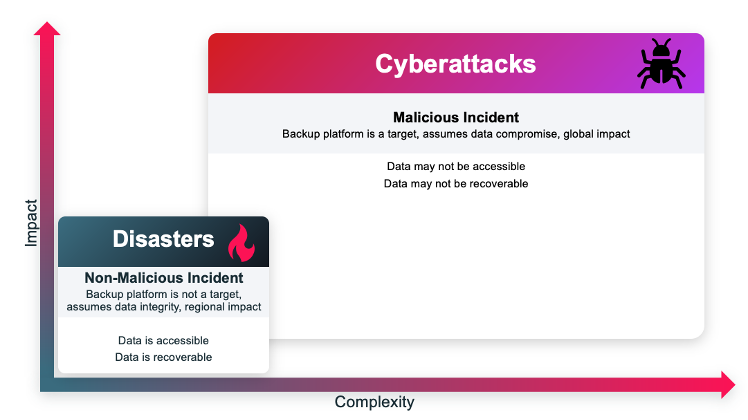
Recovery Approaches
Let's start with a traditional disaster recovery approach from backup. In a non-malicious incident, like hardware failure or accidental deletion, the backup platform isn’t a target. Recovery is straightforward with a recent backup copy. You can quickly recover right back to the original location or an alternative location. Simple. The systems you use are working and trusted.
In contrast, a cyberattack maliciously goes after anything and everything, making recovery complex. Containment is your priority. This entails stopping the attacker's access and preventing further damage immediately. By isolating the affected systems or networks, you can minimize the attack's spread and begin recovery sooner. Containment extends beyond firewalls and networks. Be sure you also consider credentials. Real-world attacks have included attackers using compromised credentials to join conference calls or listen to group chats. You’re now dealing with trust issues between teams and the very systems on which you rely, further complicating and slowing recovery operations. Forensics teams work to pinpoint how the attacker gained entry, find vulnerabilities and malware, and prevent reinfection by diagnosing which systems were potentially affected.
Concurrent with containment and forensic actions, you must address evolving business complications. In the case of ransomware, you may have specialty firms or even government agencies stepping in to negotiate with attackers. Your executive, finance, public, and investor relations teams will likely meet hourly to assess customer impact, decide who to inform, and work with insurance carriers.
All the while, legal teams specializing in privacy and compliance need to determine who they must notify and when. Meanwhile, internal communications teams need to inform employees of what’s happening. In some cases, the human resources team gets involved if the attack affects the ability to make payroll on time or results in other employee issues.
All this can be overwhelming, especially if you haven’t built out a cyber recovery plan prior to an active cyberattack. Let's walk through some of the steps to address before, during, and after an incident to help you withstand and recover from a cyberattack.
Before a Cyberattack
The more you do in advance, the easier recovery will be. Reinforcing your security posture — your ability and readiness to identify, respond, and recover from an incident — is critical to preparation. Not only will you have a greater understanding of your environment, but you’ll be able to prioritize your response.
Inventory, Classify, and Capture Data
Know what you need to protect across your environment. Inventory all your data and identify where protection policy gaps exist. Find and eliminate shadow IT and dark data throughout your environment. Classify and capture primary production data to assess what is mission-critical and Conduct sensitive data analysis.
Protect Data
Create protection and retention policies. Improve posture using security meters, scorecards, and audits. Reduce complexity by using automation and AI/ML. Ensure that you’ve backed up every production system and can restore them promptly to meet SLAs.
Assess and Harden Data Protection
Leverage zero-trust principles to improve data protection. Strengthen access controls, mplement multifactor authentication (MFA) and multiperson authentication (MPA) to control backup schedules and retention periods. Leverage role-based access control (RBAC) for user and process permissions. Encrypt data both in transit and at rest.
Isolate Important Data
Implement a modern 3-2-1 backup strategy. Create an immutable, indelible isolated copy of data and implement an isolated recovery environment (IRE) or SaaS data isolation.
Define a Recovery Plan
Create an orchestrated recovery plan across all data and all teams in your environment. This is key and is often the most challenging part of recovery today. Conduct non-disruptive recovery testing and rehearsals, including tabletop exercises. Set up teams across lines of business, security, and operations to identify appropriate recovery plans for specific functions. Automate as much as possible. Establish your recovery time objective (RTO), the maximum amount of time your mission-critical applications can be down after a disaster or cyberattack. Define your recovery point objective (RPO), the amount of data loss you can tolerate during a disaster or cyberattack.
3 Key Actions During an Attack
Assess User Activity
- Understand what is happening within your data estate at all times.
- Deploy a dashboard to observe any anomalous user activity that could indicate an active attack.
Detect Threats
- Use AI-powered anomaly detection to identify whether backup data shows indicators of an emerging ransomware attack.
- Spawn alerts to security operations.
- Begin malware scanning to triage the alert.
Conduct Impact Analysis
- Locate potentially compromised and accessed data.
4 Priorities After an Attack
Once you can start recovery, it’s vital that you don’t re-infect your data. You may feel the pressure to restore business to normal as quickly as possible. But if you accidentally restore a vulnerability or a file with malware, you must start the entire process again.
Leverage integrated malware and vulnerability scanning to assess your backup data while the security team remediates active threats. Taking a parallel approach can significantly speed decontamination and recovery.
Conduct Forensics
Your backups can often be the hero as a sort of time machine. Assess the incident’s impact on files, apps, computing, and storage. Audit everything. Prepare to report back to any teams that use the impacted systems. Evaluate where you’ve experienced partial impact or total loss. Decide who makes the difficult prioritization decisions. Prioritize recovery based on overall business impact, costs, and time duration.
Restore to an IRE and Cleanse Data
Identify the last-known good backup to ensure you have clean data to restore. Cleanse data and then check for remaining or additional vulnerabilities and threats. Again, the goal is to ensure you do not reintroduce any lingering trace of an infection.
Restore Active Directory and Identity Services
You may need to reboot foundational services like Active Directory or your Domain Name System.
Recover to Production
Deploy rapid, flexible, and orchestrated recovery and procedures to restore primary services and applications.
Prioritize Proactive Preparation
The key to success is to plan and automate your recovery plan with your security teams. Then practice, practice, practice. If you have a playbook and know that your teams are prepared for an attack, you’ll be ready to manage an actual incident. The work you do to plan for attack recovery will also help you better manage routine recovery challenges such as system outages or application failures.
Veritas helps you prevent data loss, limit downtime, and recover confidently and quickly to support business resilience. Learn about Veritas 360 Defense, a holistic approach that combines data protection, security, and governance with an expanding ecosystem of cybersecurity partners.
