Isolated Recovery Environments: The Next Thing in Cyber Recovery
Cyber threat actors aggressively seek ways to get your data and dollars. Ransomware, phishing, social engineering, and exfiltration are just some of their tactics. Unfortunately, they’re eventually bound to catch up with you with one of these approaches — or something new.
It’s simply good business to establish safeguards to prevent bad actors from taking your data or holding it for ransom. Because if they do, you’re accountable and responsible for the fallout.
What happens if you’re hit by a cyberattack today? Are you prepared to recover? You may not be able to answer that question. And in today's increasingly regulated world, you are required to acknowledge when a bad actor breaches your network.
Public companies must disclose material cybersecurity incidents within four business days. How do you know whether an incident is considered material? The answer: It depends. The list of factors to determine materiality is extensive, but examples include incidents that:
- Harm your organization’s reputation
- Compromise consumer or employee data
- Hinder your ability to provide services
This is where isolated recovery environments (IREs) come into play. Isolating your critical data can minimize your risk as part of recovering from a cybersecurity incident.
What Is an IRE?
An IRE enables air-gap backup copies by turning off network connectivity to secure your data.
Air gapping involves keeping an offline copy of important data to prevent chances of it being compromised. The air in airgap literally describes the concept of keeping a barrier between data and online access to it. Also known as an air wall, air gapping isolates the system’s network, keeping it separate from other connected devices and preventing online access to it.
Establishing an IRE gives administrators a clean set of files that they can recover on demand to neutralize the impact of a cyberattack.
Why Isolate Critical Data?
Isolate your data to better prepare for worst-case scenarios. If you have data in the cloud or on-prem, isolating data can also help you comply with specific regulations.
For example, an IRE can help banking and financial services meet Sheltered Harbor requirements. Sheltered Harbor has become essential in efforts to maintain the security and stability of the financial sector, particularly against increasing cyberattacks. Financial institutions participating in the program demonstrate their commitment to protecting consumer data and maintaining trust in their systems, both during an event and after a cyberattack.
A good IRE solution will provide the following:
- Secure backups with immutability (read-only) and indelibility (no early deletion)
- Ransomware detection to prevent reinfection during restoration
- Enterprise-level recovery at scale to meet service-level objectives (SLOs)
- Predictable recovery process rehearsal to on-premises or cloud systems
How Can You Implement an IRE?
You can spend a lot of time strategizing, planning, and architecting a solution. Or you can take advantage of an existing solution. Veritas NetBackup Isolated Recovery Environment integrates immutability and indelibility. Your data is safe leveraging Veritas Flex appliances container-based, multitenant zero-trust WORM storage. The air gap controls network access to the IRE to secure your data further (Figure 1).
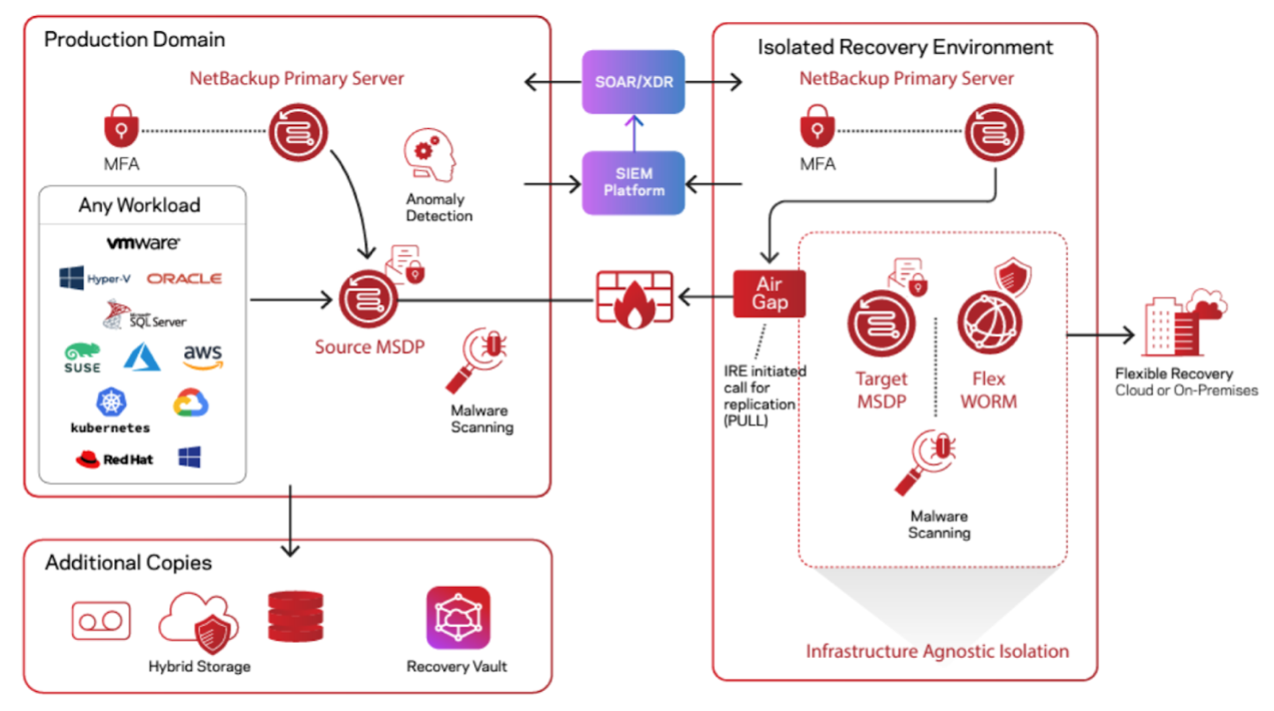
Figure 1. The air gap isolates your network from the IRE.
The Security and Privacy Controls for Information Systems and Organizations (SP 800-53) from the National Institute of Standards and Technology (NIST) provides an excellent security framework. This publication outlines security and privacy controls to protect individuals, organizations, and the nation from diverse threats. It addresses hostile attacks, human errors, natural disasters, structural failures, foreign intelligence entities, and privacy risks.
NIST provides five areas to help you reduce security risks: identification, protection, detection, response, and recovery. Use an IRE to address three of the five areas, specifically:
- Protection: Store a backup image on primary storage and replicate a second copy to WORM storage. This prevents malware from propagating into your IRE due to the air-gap network and immutable storage.
- Detection: Use anomaly detection and malware scanning to help identify backup abnormalities.
- Recovery: Maintain a secure, clean copy of critical backup data for swift recovery. With an IRE, if images within the backup are infected, your backup administrators will receive an alert and a report of those files.
Isolate Data Today to Recover Tomorrow
The ideal moment to implement data isolation is before a security incident occurs. However, there’s still time to act if an incident has already happened. You can isolate affected data to mitigate the potential impact of the breach. And you can enhance your strategy with more effective incident response and recovery efforts.
Using an IRE and data isolation in regulatory compliance efforts has several benefits, including:
- Reduced Attack Surface: Minimize the amount of data exposed to potential threats to make it more difficult for attackers to access sensitive critical systems.
- Improved Compliance: Many industry regulations and standards, such as GDPR, HIPAA, and PCI DSS, require that you implement appropriate data-protection measures for sensitive information. Data isolation is vital in achieving compliance by ensuring that you protect sensitive data and isolate it from unauthorized access.
- Increased Resilience and Business Continuity: Isolating data enhances your ability to withstand cyberattacks. Limiting or minimizing impact on a subset of systems or data helps to maintain critical functions even if a breach occurs.
What Next?
As cyberthreats increase in sophistication, so must your approach to cybersecurity. IREs have emerged as an essential strategy to protect critical data. Investing now means safeguarding your organization's future security, integrity, and resilience.
IREs represent another layer of defense. Not only do they facilitate compliance, but they emphasize your dedication to cybersecurity, helping to build trust with customers, partners, and stakeholders.
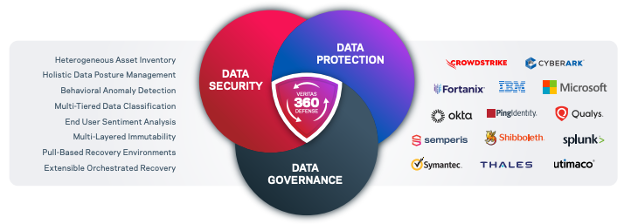
Invest in IREs today to safeguard your future. Veritas includes IREs as an integral element of Veritas 360 Defense to help you maintain resilience while improving recovery capabilities. Veritas 360 Defense incorporates the foresight and operational efficiency to ensure that data is not just backed up, but backed up and recovered intelligently, considering the ever-changing landscape of IT assets.
Next Step
Learn more about how to apply Veritas 360 Defense to keep your applications resilient and your data protected, compliant, and recoverable, when it matters most.
