Veritas 360 Defense, Get Real About Cyber Resilience
Are you ready to get real about cyber resilience? It's time. The risks to your data are vast. Why? Cyber criminals. Their sophistication and ability to cause disruption is unprecedented compared to anything we have seen in the industry.
In the past, natural disasters and human error were the leading causes of downtime and outages. Recovery was uncomplicated. Let’s say a flood wiped out a data center, for example. Data protection teams could quickly evaluate whether they needed to recover everything—from data and applications to the entire data center. They had options. Meeting a five-hour recovery time objective (RTO) was straightforward and achievable. Recovery involved only a few IT teams and was just another closed ticket and summary email for a job well done.
The Reality Today
Cyber criminals are bombarding organizations with ransomware or cyberattacks aimed at mass disruption. They’re targeting data that lives across the globe in complex, heterogeneous, multi-cloud environments and affects multiple teams, tools, and processes. The impact of such attacks can span your entire data ecosystem. Cyberattacks can infest or compromise everything. Which means business comes to a halt. Depending on your industry, that could result in public outages where hospitals cancel patients’ appointments and can’t distribute critical medicines, guests can’t check in to hotel rooms, or drivers can’t pump gas.
Meeting a five-hour RTO has become a herculean effort. And not just from a technological perspective. When malware hits, multiple teams typically manage the response using disparate tools. Attacks affect the entirety of IT: Data protection, security, and compliance teams must work together. Command centers also involve the C-level, board members, legal teams, and public relations professionals. All this can extend the time it takes to recover—or even make full recovery impossible.
How Veritas Helps
We understand the damage that downtime and data theft can cause. Our teams have been working hard to innovate and solve these challenges. We want you to be resilient. That is what is so exciting about today’s announcement.
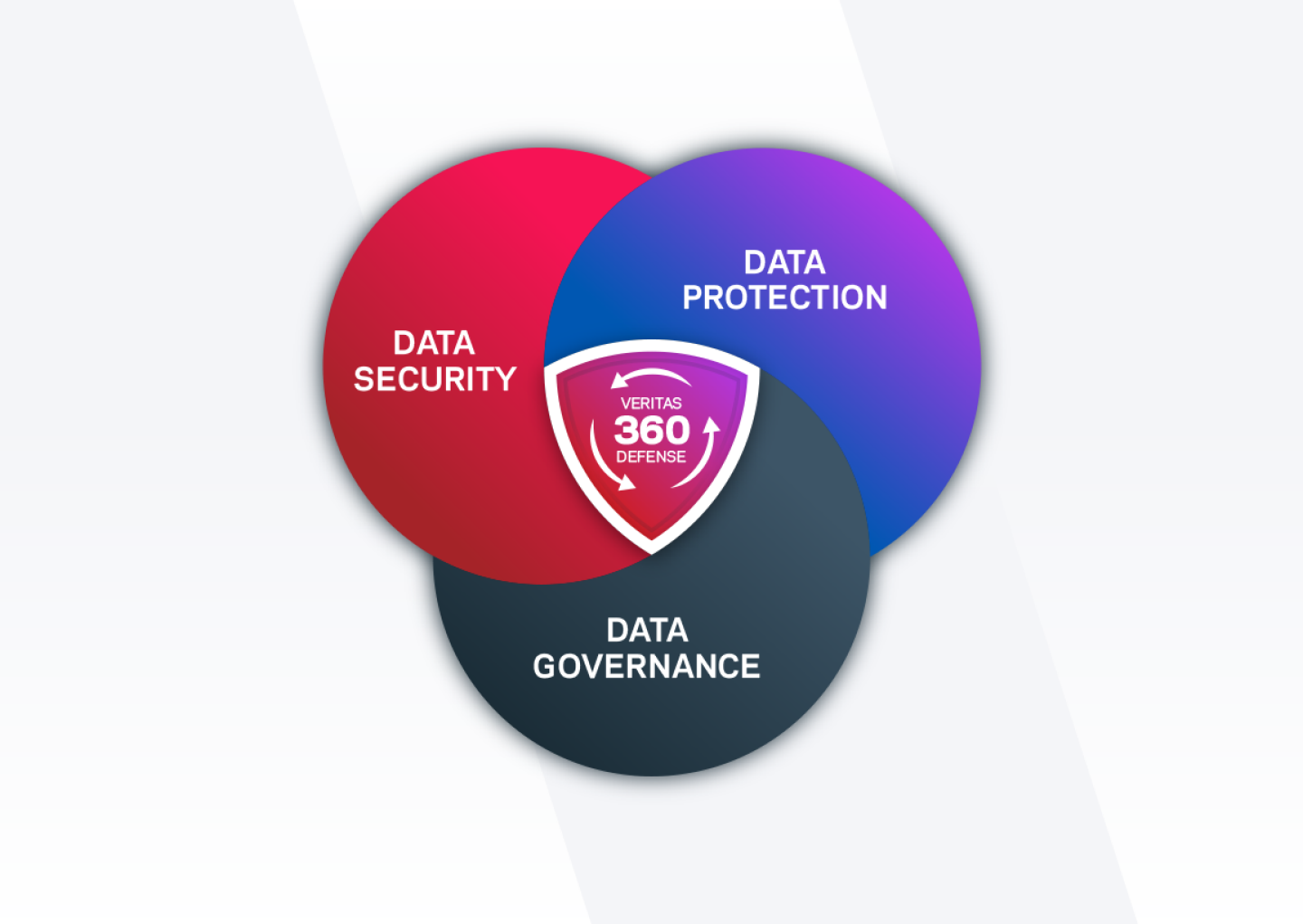
Today we announce our Veritas 360 Defense architecture, a blueprint to unite multiple disciplines to provide unmatched resilience in the face of cyber threats.
Veritas 360 Defense addresses these challenges by integrating data security, protection, and governance, providing differentiated capabilities through the Veritas portfolio and our expanding ecosystem of cybersecurity partners.
The Veritas 360 Defense
Hackers love patchwork defenses of disparate solutions because the product interaction points can become potential vulnerabilities. Strong ecosystems that undergo rigorous testing do away with the stitched-together approach, integrating solutions like links in a hardened chain. That’s what we’re offering today. We’ve partnered not only with the champions of the security world, like CyberArk and CrowdStrike, but we’re offering more, with unparalleled relationships with organizations that do things differently, such as Semperis. Check out all our partners in the Veritas Trust Center.
Watch “Getting Real About Cyber Resilience,” an announcement highlighting the unique power of the Veritas 360 Defense architecture. Learn about our latest capabilities and the extension of our ecosystem of cybersecurity partners. And hear about our one-of-a-kind, industry-first Veritas REDLab, where we “keep it real” by testing our software against the latest cyber threats.
