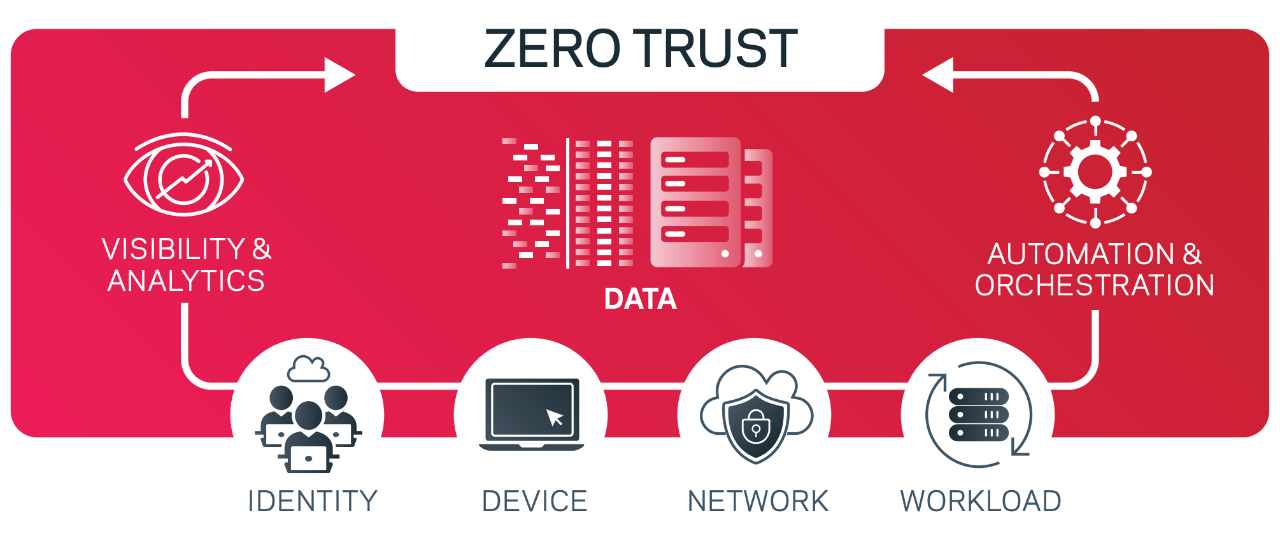
Zero Trust: Why Cyber Criminals Fear It

The threat of cyber criminals is pervasive. Bad actors have the potential to cause great harm and leave your organization in an exposed state. By proactively embracing a Zero Trust mindset — one of never trust, always verify — you can improve your cyber resilience.
Cybercriminals will go to great lengths to gain access to logins and credentials. They’ll use tactics to penetrate vulnerable entry points in your infrastructure. A zero-trust strategy secures your system with rigorous access controls.
Click to access the infographic.
Lock Down Your Data Using Zero Trust
Consider the following actions:
Identify and classify your data.
Start by gaining a comprehensive understanding of your digital assets. Include devices, applications, data, and network components. Classify and prioritize data based on sensitivity, operational impact, and business value.
Click to watch our Zero Trust TL;DR
Segment and micro-segment your network.
You can lower the impact of a data breach by breaking your network into smaller, isolated segments. Limit lateral movement within your network, in case of a breach. Micro-segmentation allows you to enforce access with features like role-based access control (RBAC).
Isolate backups and use air gaps to logically and physically separate them from the primary data center. Automating air gaps offers flexibility to move replicated information into highly secure write one, ready many (WORM) storage.
In the unfortunate event of an attack or disruption, you need reliable backups in place to quickly restore data and redress lost information. This is why immutable backups are also an important part of your defense strategy. Not only do they ensure malicious malware remains contained, but they guarantee swift recovery should disaster strike.
If you’re not already using one, consider a 3-2-1 immutable backup strategy. This approach uses three backups in two separate places, with at least one in an immutable off-site location. Separating backups from the main system reduces the chances of malware spreading. Veritas automates keeping backups safe, compliant with regulations, and secure from unauthorized access or tampering.
Implement access management.
A robust identity and access management (IAM) practice includes multi-factor authentication (MFA), strong password policies, and just-in-time access. Grant users the least privilege necessary to perform tasks. Regularly review access and revoke access as needed. Veritas solutions have a digitally signed process and secure architecture that guarantees only allowed processes execute on the system.
Monitor your network, devices, and data.
Be vigilant for signs of unauthorized access and suspicious activity. AI and machine learning can detect data anomalies and malware, allowing you to identify potential threats in real time to quickly respond and contain breaches.
Veritas alerts administrators to take immediate action against possible malicious activity as it evaluates backup jobs in near real time. AI-based anomaly detection alerts you to unexpected changes, ensuring you can take action before a lock-out occurs. This capability is available on any NetBackup server and doesn’t need additional infrastructure for post-processing.
Secure applications.
Protect your applications with strong authentication and authorization. Utilize an isolated recovery environment (IRE), air gaps, and data vaults. An IRE separates the most important data from the rest of the system. This way, if someone does attack the system, they can’t access that critical data. An IRE also focuses on containment and limiting impact of a breach, and helping you meet regulatory compliance of continuous verification and strict access control.
While the IRE keeps bad actors out, Veritas also uses an immutable data vault to keep your intact as long as you need it. This is where your air gap resides. It’s a safe place where no one can change or destroy the data. An IRE is often an extra cost, but it can be a built-in element of your Veritas solution. With no additional infrastructure or licensing costs, it’s an opportunity to lower your total cost of operations. Veritas appliances also employ AES 256-bit encryption for data in motion and at rest, with optional client encryption for additional peace of mind. Veritas also satisfies FIPS 140-2 requirements for government compliance.
For added security, you can deploy an intrusion prevention system (IPS) or intrusion detection system (IDS). An IPS/IDS focuses on continuous monitoring, strict access controls, and verification of network activities. It can enhance the effectiveness of your Zero Trust strategy by focusing on threat detection.
Audit systems and test your recovery strategy.
Continuously review and evaluate your Zero Trust strategy to identify vulnerabilities. This allows you to optimize for the best data protection and swift recovery and availability. Align your resources to your operational priorities to maintain resiliency and continuity.
Get Started
Adopting a Zero Trust approach creates a cybersecurity framework that aligns with the principles of resilience — the ability to withstand, respond, and recover from disruptions. Zero Trust’s emphasis on continuous verification and access helps minimize the attack surface, detect threats early, and reduce the impact of incidents. Remember that cyber resilience is an ongoing effort requiring constant adaptation and improvement as the threat landscape evolves.